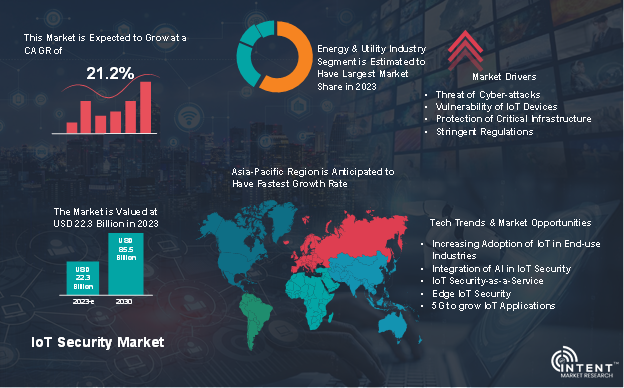
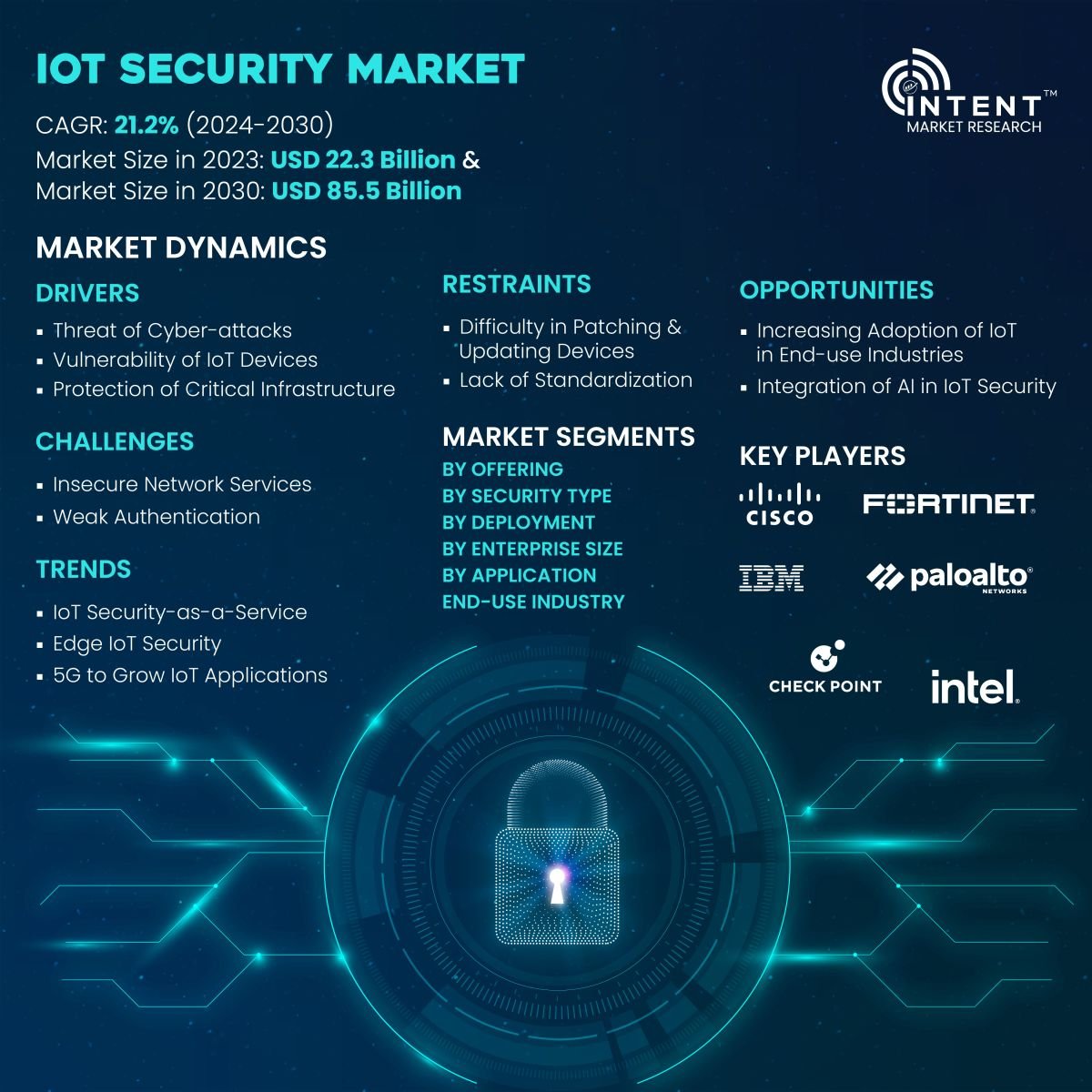
The IoT security market is expected to grow from USD 22.3 billion in 2023-e to USD 85.5 billion by 2030, at a CAGR of 21.2% during the forecast period. The IoT security market is a competitive market, the prominent players in the global market include Allot, Check Point, Cisco, Fortinet, IBM, Intel, Microsoft, Palo Alto, Thales, and Trend Micro. Additionally, Afero, Bastille Networks, Claroty, Cybeats, Nozomi Networks, Nubeva Technologies, Ordr, SAM Seamless Network, Xage Security, and Zscaler are emerging companies in the global IoT security market.
As per Intent Market Research, the global IoT (Internet of Things) security market accounted for USD 22.3 billion in 2023-e and is projected to reach USD 85.5 billion by 2030, growing at a CAGR of 21.2% from 2024 to 2030.
IoT security is built on a cybersecurity approach that prevents cyberattacks on IoT devices and the insecure networks they link to. IoT devices have no built-in security and IoT security is needed to help prevent data breaches as these IoT devices transfer data over the internet unencrypted and operate undetected by standard cybersecurity systems.
The IoT encompasses a vast array of physical devices, sensors, actuators, and software that communicate with each other and with centralized systems through the internet. IoT security is essential to safeguard these devices and the data they generate from potential cyber threats and unauthorized access.
Increasing Threat of Cyber-attacks is Promoting IoT Security Market
The increasing threat of cyber-attacks is promoting the adoption of IoT security measures. As the number of connected devices continues to grow, so does the attack surface for potential cyber threats. The rapid growth of IoT devices across various industries and sectors leads to a larger attack surface. Each connected device represents a potential entry point for cybercriminals.
Check Point estimated, on average, every week 54% of organizations suffer from attempted cyber-attacks targeting IoT devices. The first two months of 2023 have seen a 41% increase in the average number of weekly attacks per organization targeting IoT devices, compared to 2022.

Source: Check Point Software Technologies Ltd.
The recognition of these issues and the growing awareness of the potential consequences of cyber-attacks on IoT devices are driving organizations to invest in comprehensive IoT security solutions. These solutions encompass device authentication, secure communication, regular software updates, and the implementation of industry best practices to mitigate cyber threats and enhance the overall resilience of IoT ecosystems.
IoT Security Market Segment Insights
High Demand for IoT Security Solutions is Driving the Market Growth
Several security solutions are driving the IoT security market as organizations seek comprehensive measures to protect their interconnected devices, networks, and data. These solutions address various aspects of IoT security, aiming to mitigate vulnerabilities and safeguard against cyber threats. Solutions such as identity & access management (IAM), data encryption & tokenization, and DDoS protection solutions are the preferred solutions for IoT security.
IAM systems facilitate the authentication of IoT devices, ensuring that only trusted and authorized devices can connect to the network and communicate with other devices or services. Device authentication prevents unauthorized devices from accessing the IoT ecosystem, reducing the risk of malicious activities and unauthorized data access. Data encryption and tokenization are crucial security measures used in the context of the Internet of Things (IoT) to safeguard sensitive information and protect the integrity and confidentiality of data. In addition, DDoS protection solutions continuously monitor network traffic for patterns and anomalies. They use traffic analysis to distinguish between normal and potentially malicious activities. Such benefits offered by the IoT security solutions are driving the market growth.
Greater Emphasis on Network Security Dominating the Segment Growth
The growth of IoT network security is an essential component of the broader effort to create a secure and trustworthy IoT environment. As the IoT landscape evolves, organizations, manufacturers, and policymakers continue to work together to address security challenges and establish standards that prioritize the protection of IoT devices and the networks they operate on. Network security has captured a significant share of the market in 2023.
Increased Penetration of Cloud Expected to Drive the Segmental Growth
Cloud service providers offer specialized security services that organizations can leverage to enhance the security of their IoT deployments. This includes services such as identity and access management, encryption, and threat detection. The cloud introduces a dynamic threat landscape, with attackers continuously evolving their tactics. Cloud-based IoT security solutions must be adaptive and capable of detecting and mitigating emerging threats in real-time.
As the adoption of cloud services in IoT environments continues to grow, organizations are investing in comprehensive IoT security solutions to address the specific challenges introduced by cloud-based deployments. Ensuring the confidentiality, integrity, and availability of data in the interconnected world of IoT and cloud computing is a priority for organizations seeking to harness the benefits of both technologies securely.
SMEs Expected to Rapidly Adopt IoT Security
SMEs are becoming more aware of the potential security risks associated with IoT deployments. Cyber threats, data breaches, and the potential compromise of sensitive information are driving SMEs to prioritize security as an integral component of their IoT strategies. SMEs, such as larger enterprises, are becoming more dependent on digital technologies to conduct business. This digital transformation includes the use of IoT devices, making security a critical aspect of safeguarding business continuity and customer trust.
IoT security solutions are becoming more accessible and integrated into broader IoT offerings. As a result, SMEs can leverage comprehensive and user-friendly security solutions that align with their specific needs without requiring extensive expertise. These factors will drive the growth of SMEs and are expected to grow rapidly in the coming years.
Industry 4.0 to Drive Smart Manufacturing Segment
Industry 4.0 leverages a multitude of connected devices and IoT sensors to collect real-time data from various points in the manufacturing process. The proliferation of these devices increases the attack surface, making robust security essential to protect against potential threats. It emphasizes data-driven decision-making through the analysis of large datasets generated by IoT devices. Protecting the integrity and confidentiality of this data is critical to ensure the accuracy and reliability of decision-making processes.
The increasing complexity and connectivity in smart manufacturing underscore the imperative to prioritize IoT security measures to ensure the resilience, reliability, and security of the entire manufacturing ecosystem. Governments and regulatory bodies are recognizing the importance of security in smart manufacturing. Compliance with regulations related to data protection and cybersecurity is becoming a key driver for implementing robust IoT security. In 2023, the smart manufacturing segment is estimated to capture the major share of the market.
eHealth to Promote Healthcare Industry with Rapid Growth
The integration of eHealth solutions is expected to play a significant role in promoting and driving the implementation of robust Internet of Things (IoT) security measures in the healthcare industry. eHealth facilitates remote patient monitoring through IoT devices that collect and transmit health data. Ensuring the security of these devices and the communication channels is essential to protect patient privacy and maintain data integrity.
The healthcare industry is subject to strict regulatory requirements related to patient data protection and privacy, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States. Adhering to these regulations drives the implementation of IoT security measures. Additionally, the Internet of Medical Things (IoMT) ecosystem is essential to prevent cyber threats that could compromise patient safety and privacy. The growing adoption of IoT in the healthcare industry is expected to drive the segment with a significant CAGR during the forecast period.
Asia-Pacific to Grow Exponentially in the Coming Years
The Asia-Pacific region is witnessing rapid adoption of IoT technologies in industries such as manufacturing, healthcare, agriculture, smart cities, and logistics. The proliferation of IoT devices increases the attack surface, driving the need for robust security measures. Industries in the Asia-Pacific, including manufacturing, energy, and utilities, are embracing Industrial IoT (IIoT) for automation and efficiency. Securing industrial processes and critical infrastructure becomes imperative to prevent disruptions and protect sensitive data.
Many cities in the Asia-Pacific are investing in smart city initiatives, deploying IoT devices for urban infrastructure, transportation, and public services. The interconnected nature of these systems necessitates comprehensive security measures to safeguard critical infrastructure. The healthcare industry in the Asia-Pacific is adopting IoT for connected healthcare solutions, including remote patient monitoring and digital health records. Securing healthcare data and ensuring patient privacy drive the implementation of IoT security measures. All these factors are expected to drive the regional market growth during the forecast period.

Source: Intent Market Research Analysis
Major Industry Players are Enhancing their Market Positions By Adopting M&A Strategies
Major players operating in the global IoT security market are Allot, Check Point, Cisco, Fortinet, IBM, Intel, Microsoft, Palo Alto, Thales, and Trend Micro. Additionally, Afero, Bastille Networks, Claroty, Cybeats, Nozomi Networks, Nubeva Technologies, Ordr, SAM Seamless Network, Xage Security, and Zscaler are emerging companies in the global IoT security market.
To tap the potential share of the market, major players have started adopting strategies such as new product launches, mergers & acquisitions, partnerships & collaboration. Some of the significant developments are mentioned below:
- In July 2023, Cynerio and Check Point Software Technologies announced a partnership to provide healthcare organizations with comprehensive security for their medical IoT devices. Cynerio's 360 platform will provide functionality critical to securing healthcare IoT devices including device discovery, patch guidance, micro-segmentation, and attack detection.
- In August 2023, Fortinet expanded its security portfolio with new hardware and software designed to protect resources attached to industrial networks.
IoT Security Market Coverage
The report provides key insights into the IoT security market, and it focuses on technological developments, trends, and initiatives taken by the government and private players. It delves into market drivers, restraints, opportunities, and challenges that are impacting market growth. It analyses key players as well as the competitive landscape within the global market.

Report Scope:
|
Report Features |
Description |
|
Market Size (2023-e) |
USD 22.3 billion |
|
Forecast Revenue (2030) |
USD 85.5 billion |
|
CAGR (2024-2030) |
21.2% |
|
Base Year for Estimation |
2023-e |
|
Historic Year |
2022 |
|
Forecast Period |
2024-2030 |
|
Report Coverage |
Market Forecast, Market Dynamics, Competitive Landscape, Recent Developments |
|
Segments Covered |
By Offering (Solution (Identity & Access Management, Security Analytics, IDS/IPS, Data Encryption & Tokenization, DDoS Protection Solution, Unified Threat Management, Other Solutions), Services); By Security Type (Network Security, Cloud Security, End-point Security, Application Security, Others); By Deployment (Cloud, On-premise); By Enterprise Size (SMEs, Large Enterprises); By Application (Smart Manufacturing, Smart Utilities, Connected Logistics, Smart City, Smart Healthcare, Smart Retail, Smart Agriculture, Smart Surveillance, Others); By End-use Industry (Manufacturing, Energy & Utilities, Transport & Logistics, Consumer Electronics, Healthcare, Retail & E-commerce, Agriculture, Building & Construction, Security & Defense, Other Industries) |
|
Regional Analysis |
North America (US, Canada), Asia-Pacific (China, Japan, South Korea, India), Europe (Germany, France, UK, Italy), Latin America and Middle East & Africa |
|
Competitive Landscape |
Allot, Check Point, Cisco, Fortinet, IBM, Intel, Microsoft, Palo Alto, Thales, Trend Micro, Afero, Bastille Networks, Claroty, Cybeats, Nozomi Networks, Nubeva Technologies, SAM Seamless Network, Xage Security, and Zscaler |
|
Customization Scope |
Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements |
|
Purchase Options |
We have three licenses to opt for Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) |
|
1.Introduction |
|
1.1.Market Definition |
|
1.2.Scope of the Study |
|
1.3.Key Stakeholders of the Market |
|
2.Research Methodology |
|
2.1.Research Approach |
|
2.2.Data Collection |
|
2.3.Market Assessment |
|
2.4.Assumptions & Limitations for the Study |
|
3.Executive Summary |
|
4.Market Dynamics |
|
4.1.Drivers |
|
4.1.1.Threat of Cyber-attacks |
|
4.1.2.Vulnerability of IoT Devices |
|
4.1.3.Protection of Critical Infrastructure |
|
4.1.4.Stringent Regulations |
|
4.2.Restraints |
|
4.2.1.Difficulty in Patching and Updating Devices |
|
4.2.2.Lack of Standardization |
|
4.3.Opportunities |
|
4.3.1.Increasing Adoption of IoT in End-use Industries |
|
4.3.2.Integration of AI in IoT Security |
|
4.3.3.Blockchain for IoT Security |
|
4.4.Challenges |
|
4.4.1.Insecure Network Services |
|
4.4.2.Weak Authentication |
|
4.5.Trends |
|
4.5.1.IoT Security-as-a-Service |
|
4.5.2.Edge IoT Security |
|
4.5.3.5G to Grow IoT Applications |
|
5.Market Outlook |
|
5.1.Regulatory Analysis |
|
5.2.Pricing Analysis |
|
5.3.PESTLE Analysis |
|
5.4.PORTER's Five Forces Analysis |
|
5.5.Case Studies |
|
6.Market Size by Offering (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
6.1.Solutions |
|
6.1.1.Identity & Access Management |
|
6.1.2.Security Analytics |
|
6.1.3.IDS/IPS |
|
6.1.4.Data Encryption & Tokenization |
|
6.1.5.DDoS Protection Solution |
|
6.1.6.Unified Threat Management |
|
6.1.7.Other Solutions |
|
6.2.Services |
|
6.2.1.Professional Services |
|
6.2.2.Managed Services |
|
7.Market Size by Security Type (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
7.1.Network Security |
|
7.2.Cloud Security |
|
7.3.End-point Security |
|
7.4.Application Security |
|
7.5.Other Types |
|
8.Market Size by Deployment (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
8.1.Cloud |
|
8.2.On-premise |
|
9.Market Size by Enterprise Size (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
9.1.SMEs |
|
9.2.Large Enterprises |
|
10.Market Size by Application (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
10.1. Smart Manufacturing |
|
10.2. Smart Utilities |
|
10.3. Connected Logistics |
|
10.4. Smart City |
|
10.5. Smart Healthcare |
|
10.6. Smart Retail |
|
10.7. Smart Agriculture |
|
10.8. Smart Surveillance |
|
10.9. Other Applications |
|
11.Market Size by End-use Industries (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
11.1. Manufacturing |
|
11.2. Energy & Utility |
|
11.3. Transport & Logistics |
|
11.4. Consumer Electronics |
|
11.5. Healthcare |
|
11.6. Retail & E-commerce |
|
11.7. Agriculture |
|
11.8. Building & Construction |
|
11.9. Security & Defense |
|
11.10. Other Industries |
|
12.Regional Outlook (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
12.1. North America |
|
12.1.1. US |
|
12.1.1.1. US Market Outlook by Offering |
|
12.1.1.2. US Market Outlook by Security Type |
|
12.1.1.3. US Market Outlook by Deployment |
|
12.1.1.4. US Market Outlook by Organization Size |
|
12.1.1.5. US Market Outlook by Application |
|
12.1.1.6. US Market Outlook by End-use Industries |
|
Note: Similar Cross-segmentation for each country will be covered as shown above |
|
12.1.2. Canada |
|
12.2. Asia-Pacific |
|
12.2.1. China |
|
12.2.2. Japan |
|
12.2.3. South Korea |
|
12.2.4. India |
|
12.3. Europe |
|
12.3.1. UK |
|
12.3.2. Germany |
|
12.3.3. France |
|
12.3.4. Italy |
|
12.4. Latin America |
|
12.5. Middle East & Africa |
|
13.Competitive Landscape |
|
13.1. Market Share Analysis |
|
13.2. Key Market Growth Strategies |
|
13.3. Company Strategy Analysis |
|
13.4. Competitive Benchmarking |
|
14.Company Profile |
|
14.1. Allot |
|
14.2. Check Point |
|
14.3. Cisco |
|
14.4. Fortinet |
|
14.5. IBM |
|
14.6. Intel |
|
14.7. Microsoft |
|
14.8. Palo Alto |
|
14.9. Thales |
|
14.10. Trend Micro |
|
15.Emerging Companies |
|
15.1. Afero |
|
15.2. Bastille Networks |
|
15.3. Claroty |
|
15.4. Cybeats |
|
15.5. Nozomi Networks |
|
15.6. Nubeva Technologies |
|
15.7. Ordr |
|
15.8. SAM Seamless Network |
|
15.9. Xage Security |
|
15.10. Zscaler |
|
16.Appendix |
Let us connect with you TOC
Intent Market Research employs a rigorous methodology to minimize residual errors by carefully defining the scope, validating findings through primary research, and consistently updating our in-house database. This dynamic approach allows us to capture ongoing market fluctuations and adapt to evolving market uncertainties.
The research factors used in our methodology vary depending on the specific market being analysed. To begin with, we incorporate both demand and supply side information into our model to identify and address market gaps. Additionally, we also employ approaches such as Macro-indicator Analysis, Factor Analysis, Value Chain-based Sizing, and forecasting to further increase the accuracy of the numbers and validate the findings.
Research Approach

- Secondary Research Approach: During the initial phase of the research process, we acquire and accumulate extensive data continuously. This data is carefully filtered and validated through a variety of secondary sources.
- Primary Research Approach: Following the consolidation of data gathered through secondary research, we initiate a validation process to verify all the market numbers, and assumptions and validate the findings by engaging with subject matter experts.
Data Collection, Analysis and Interpretation:

Research Methodology
Our market research methodology utilizes both top-down and bottom-up approaches to segment and estimate quantitative aspects of the market. We also employ multi-perspective analysis, examining the market from distinct viewpoints.

Available Formats


