As per Intent Market Research, the Phishing Simulator Market was valued at USD 1.9 Billion in 2024-e and will surpass USD 4.7 Billion by 2030; growing at a CAGR of 16.2% during 2025-2030.
The phishing simulator market is gaining substantial traction as organizations seek to bolster their cybersecurity posture in an era where phishing attacks are increasingly sophisticated and widespread. Phishing, a form of cyberattack in which attackers deceive individuals into revealing sensitive information, remains one of the most common and damaging threats to businesses across various industries. As the frequency and complexity of these attacks continue to rise, businesses are investing heavily in training their employees to recognize and defend against such threats. Phishing simulators serve as a crucial tool in this effort, enabling organizations to create realistic simulated phishing scenarios that help employees understand potential risks and learn how to avoid them.
As cybersecurity awareness grows, the demand for phishing simulators is expanding, with businesses focusing on reducing human errors—often the weakest link in their defense mechanisms. These simulators allow companies to assess their employees' ability to identify phishing emails, offer real-time feedback, and track improvement over time. Phishing simulators are offered in various deployment modes, primarily cloud-based and on-premises, to cater to the specific needs of organizations of all sizes. Furthermore, different sectors such as BFSI, IT and telecom, retail, healthcare, and government are increasingly adopting phishing simulators to secure sensitive data, comply with regulations, and mitigate the risks associated with cyberattacks.
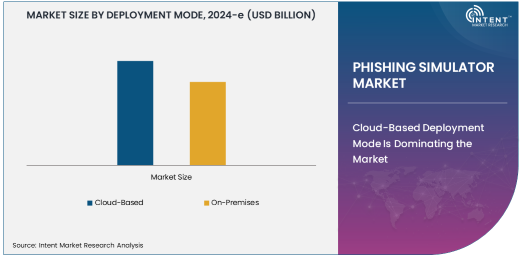
Cloud-Based Deployment Mode Is Dominating the Market
Cloud-based phishing simulators are rapidly gaining ground in the market due to their scalability, ease of access, and cost-effectiveness. As organizations continue to shift towards cloud-based IT infrastructure, they are naturally gravitating towards cloud-based cybersecurity solutions, including phishing simulators. This deployment mode offers several advantages, including automatic software updates, seamless integration with other cloud-based tools, and reduced IT maintenance requirements. Cloud-based simulators are particularly appealing for organizations with distributed teams or those operating in different geographical regions, as they allow for easy access from anywhere with an internet connection.
The increasing adoption of cloud technology across industries also fuels the growth of cloud-based phishing simulators. With the ability to rapidly deploy simulations, track employee progress in real-time, and access detailed reports and analytics, these simulators offer a high level of flexibility and efficiency for businesses. Additionally, cloud-based solutions provide cost advantages, as organizations only pay for what they use, making them an ideal choice for small to medium-sized enterprises (SMEs) and large enterprises alike. The simplicity of managing cloud-based phishing simulation programs, combined with their wide range of features and accessibility, positions them as the dominant deployment mode in the market.
BFSI Sector Leads the Adoption of Phishing Simulators
The BFSI (Banking, Financial Services, and Insurance) sector is the largest adopter of phishing simulators, driven by the sensitive nature of the data handled and the high stakes involved in maintaining robust cybersecurity. Banks, insurance companies, and other financial institutions are prime targets for phishing attacks due to the wealth of sensitive information they manage, including personal and financial data. The BFSI industry is increasingly adopting phishing simulation tools as part of its overall cybersecurity training programs to ensure that employees can identify phishing threats before they compromise sensitive systems.
The financial services industry faces increasing regulatory pressure to protect customer data and prevent data breaches, further encouraging the widespread implementation of phishing simulators. In addition to the direct threat to data security, a successful phishing attack could damage the reputation of a financial institution and lead to regulatory fines. As a result, BFSI companies are investing in phishing simulators to educate employees, reduce human error, and improve their ability to respond to phishing threats. The sector’s large-scale adoption of phishing simulators is expected to continue, driven by a combination of regulatory requirements, the need to protect sensitive information, and the constant evolution of phishing tactics.
Large Enterprises Dominate the Market
Large enterprises are the largest segment in the phishing simulator market, primarily due to their complex organizational structures and the high volume of sensitive data they handle. These enterprises often operate in multiple regions and have large numbers of employees, making it more challenging to ensure consistent cybersecurity awareness across the organization. Phishing simulators enable large organizations to conduct regular security training across all departments and geographies, ensuring that employees at every level understand the risks associated with phishing attacks. Furthermore, large enterprises often have dedicated cybersecurity teams and budgets, allowing them to invest in advanced tools and platforms to enhance their security measures.
In addition, large enterprises are more likely to have the resources to deploy on-premises phishing simulators, which offer greater control over the data and the ability to tailor simulations to the specific needs of the organization. However, even in cases where large organizations choose cloud-based solutions, they are likely to adopt more comprehensive and customized phishing simulation programs to protect their vast networks and sensitive data. As phishing attacks continue to evolve, large enterprises are expected to remain a key driver of market growth, with a focus on employee training, policy enforcement, and vulnerability assessments to mitigate risks.
Healthcare Sector Exhibits Strong Growth Potential
The healthcare sector is expected to experience rapid growth in the adoption of phishing simulators due to the increasing frequency of cyberattacks targeting healthcare providers and the growing awareness of the need to protect sensitive health data. Healthcare institutions, including hospitals, clinics, and pharmaceutical companies, are prime targets for phishing attacks, with patient data, medical records, and financial information being highly sought after by cybercriminals. Additionally, healthcare organizations are subject to stringent regulations such as HIPAA (Health Insurance Portability and Accountability Act), which mandates the protection of patient data.
Phishing simulators are becoming a vital tool in healthcare organizations’ cybersecurity strategies, helping employees recognize phishing attempts that could compromise confidential medical data. With the increasing reliance on digital health systems, electronic health records (EHRs), and telemedicine services, the adoption of phishing simulators in healthcare will continue to grow. By using these simulators, healthcare institutions can improve their employees' ability to identify phishing threats and comply with cybersecurity standards, reducing the risk of data breaches and ensuring patient trust.
Asia Pacific Is Fastest Growing Region Owing to Rising Cyber Threats
The Asia Pacific region is the fastest growing in the phishing simulator market, fueled by rising cyber threats, increasing digitization, and expanding IT infrastructure. Countries such as China, India, and Japan are witnessing a surge in phishing attacks, prompting organizations to adopt proactive cybersecurity measures. Additionally, the rapid growth of industries such as BFSI, IT, and telecom in the region is driving the demand for phishing simulation platforms.
Governments and organizations in Asia Pacific are increasingly emphasizing employee training and awareness to combat phishing attacks. The growing adoption of cloud-based solutions in the region further accelerates the adoption of phishing simulators. As small and medium enterprises (SMEs) in Asia Pacific continue to enhance their cybersecurity posture, the market is poised for significant growth in the coming years.

Competitive Landscape: Leading Players in the Phishing Simulator Market
The phishing simulator market is highly competitive, with several key players offering comprehensive solutions designed to improve cybersecurity awareness and training. Leading companies in the market include KnowBe4, Proofpoint, Cofense, and Barracuda Networks. These companies provide phishing simulation platforms that are customizable, scalable, and feature-rich, offering organizations the ability to simulate a wide range of phishing scenarios to test and train employees.
The competitive landscape is marked by innovation and product diversification, with players focusing on developing user-friendly interfaces, advanced analytics, and reporting tools to enhance the effectiveness of their phishing simulations. Some companies are also integrating machine learning and artificial intelligence into their platforms to create more realistic and adaptive phishing scenarios. Partnerships, acquisitions, and strategic collaborations are common strategies employed by market leaders to expand their reach and enhance their product offerings. As organizations continue to prioritize cybersecurity training, the competition within the phishing simulator market will likely intensify, driving further advancements in the solutions offered.
Recent Developments:
- KnowBe4 launched new phishing simulation modules that integrate advanced artificial intelligence for more realistic attack simulations.
- Proofpoint introduced a new phishing training program that enhances user engagement and effectiveness in identifying phishing emails.
- Cofense expanded its phishing simulation tools to support multi-language campaigns, increasing global accessibility for organizations.
- Trend Micro upgraded its phishing detection and simulation platform, integrating machine learning for more accurate threat identification.
- Barracuda Networks announced a partnership with leading cybersecurity firms to enhance phishing simulation capabilities within their cloud security platforms.
List of Leading Companies:
- KnowBe4
- PhishLabs
- Cofense
- Barracuda Networks
- Trend Micro
- Proofpoint
- Cyberbit
- AhnLab, Inc.
- Rapid7
- SimSpace
- Microsoft
- Webroot (A OpenText Company)
- Barracuda Networks, Inc.
- Forcepoint
- Security Mentor, Inc.
Report Scope:
|
Report Features |
Description |
|
Market Size (2024-e) |
USD 1.9 Billion |
|
Forecasted Value (2030) |
USD 4.7 Billion |
|
CAGR (2025 – 2030) |
16.2% |
|
Base Year for Estimation |
2024-e |
|
Historic Year |
2023 |
|
Forecast Period |
2025 – 2030 |
|
Report Coverage |
Market Forecast, Market Dynamics, Competitive Landscape, Recent Developments |
|
Segments Covered |
Phishing Simulator Market By Deployment Mode (Cloud-Based, On-Premises), By Component (Solution, Service), By End-Use Industry (BFSI, IT and Telecom, Retail, Healthcare, Government, Manufacturing), By Organization Size (Small and Medium Enterprises, Large Enterprises) |
|
Regional Analysis |
North America (US, Canada, Mexico), Europe (Germany, France, UK, Italy, Spain, and Rest of Europe), Asia-Pacific (China, Japan, South Korea, Australia, India, and Rest of Asia-Pacific), Latin America (Brazil, Argentina, and Rest of Latin America), Middle East & Africa (Saudi Arabia, UAE, Rest of Middle East & Africa) |
|
Major Companies |
KnowBe4, PhishLabs, Cofense, Barracuda Networks, Trend Micro, Proofpoint, Cyberbit, AhnLab, Inc., Rapid7, SimSpace, Microsoft, Webroot (A OpenText Company), Barracuda Networks, Inc., Forcepoint, Security Mentor, Inc. |
|
Customization Scope |
Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements |
|
1. Introduction |
|
1.1. Market Definition |
|
1.2. Scope of the Study |
|
1.3. Research Assumptions |
|
1.4. Study Limitations |
|
2. Research Methodology |
|
2.1. Research Approach |
|
2.1.1. Top-Down Method |
|
2.1.2. Bottom-Up Method |
|
2.1.3. Factor Impact Analysis |
|
2.2. Insights & Data Collection Process |
|
2.2.1. Secondary Research |
|
2.2.2. Primary Research |
|
2.3. Data Mining Process |
|
2.3.1. Data Analysis |
|
2.3.2. Data Validation and Revalidation |
|
2.3.3. Data Triangulation |
|
3. Executive Summary |
|
3.1. Major Markets & Segments |
|
3.2. Highest Growing Regions and Respective Countries |
|
3.3. Impact of Growth Drivers & Inhibitors |
|
3.4. Regulatory Overview by Country |
|
4. Phishing Simulator Market, by Deployment Mode (Market Size & Forecast: USD Million, 2023 – 2030) |
|
4.1. Cloud-Based |
|
4.2. On-Premises |
|
5. Phishing Simulator Market, by Component (Market Size & Forecast: USD Million, 2023 – 2030) |
|
5.1. Solution |
|
5.2. Service |
|
6. Phishing Simulator Market, by End-Use Industry (Market Size & Forecast: USD Million, 2023 – 2030) |
|
6.1. BFSI (Banking, Financial Services, and Insurance) |
|
6.2. IT and Telecom |
|
6.3. Retail |
|
6.4. Healthcare |
|
6.5. Government |
|
6.6. Manufacturing |
|
6.7. Others |
|
7. Phishing Simulator Market, by Organization Size (Market Size & Forecast: USD Million, 2023 – 2030) |
|
7.1. Small and Medium Enterprises (SMEs) |
|
7.2. Large Enterprises |
|
8. Regional Analysis (Market Size & Forecast: USD Million, 2023 – 2030) |
|
8.1. Regional Overview |
|
8.2. North America |
|
8.2.1. Regional Trends & Growth Drivers |
|
8.2.2. Barriers & Challenges |
|
8.2.3. Opportunities |
|
8.2.4. Factor Impact Analysis |
|
8.2.5. Technology Trends |
|
8.2.6. North America Phishing Simulator Market, by Deployment Mode |
|
8.2.7. North America Phishing Simulator Market, by Component |
|
8.2.8. North America Phishing Simulator Market, by End-Use Industry |
|
8.2.9. North America Phishing Simulator Market, by Organization Size |
|
8.2.10. By Country |
|
8.2.10.1. US |
|
8.2.10.1.1. US Phishing Simulator Market, by Deployment Mode |
|
8.2.10.1.2. US Phishing Simulator Market, by Component |
|
8.2.10.1.3. US Phishing Simulator Market, by End-Use Industry |
|
8.2.10.1.4. US Phishing Simulator Market, by Organization Size |
|
8.2.10.2. Canada |
|
8.2.10.3. Mexico |
|
*Similar segmentation will be provided for each region and country |
|
8.3. Europe |
|
8.4. Asia-Pacific |
|
8.5. Latin America |
|
8.6. Middle East & Africa |
|
9. Competitive Landscape |
|
9.1. Overview of the Key Players |
|
9.2. Competitive Ecosystem |
|
9.2.1. Level of Fragmentation |
|
9.2.2. Market Consolidation |
|
9.2.3. Product Innovation |
|
9.3. Company Share Analysis |
|
9.4. Company Benchmarking Matrix |
|
9.4.1. Strategic Overview |
|
9.4.2. Product Innovations |
|
9.5. Start-up Ecosystem |
|
9.6. Strategic Competitive Insights/ Customer Imperatives |
|
9.7. ESG Matrix/ Sustainability Matrix |
|
9.8. Manufacturing Network |
|
9.8.1. Locations |
|
9.8.2. Supply Chain and Logistics |
|
9.8.3. Product Flexibility/Customization |
|
9.8.4. Digital Transformation and Connectivity |
|
9.8.5. Environmental and Regulatory Compliance |
|
9.9. Technology Readiness Level Matrix |
|
9.10. Technology Maturity Curve |
|
9.11. Buying Criteria |
|
10. Company Profiles |
|
10.1. KnowBe4 |
|
10.1.1. Company Overview |
|
10.1.2. Company Financials |
|
10.1.3. Product/Service Portfolio |
|
10.1.4. Recent Developments |
|
10.1.5. IMR Analysis |
|
*Similar information will be provided for other companies |
|
10.2. PhishLabs |
|
10.3. Cofense |
|
10.4. Barracuda Networks |
|
10.5. Trend Micro |
|
10.6. Proofpoint |
|
10.7. Cyberbit |
|
10.8. AhnLab, Inc. |
|
10.9. Rapid7 |
|
10.10. SimSpace |
|
10.11. Microsoft |
|
10.12. Webroot (A OpenText Company) |
|
10.13. Barracuda Networks, Inc. |
|
10.14. Forcepoint |
|
10.15. Security Mentor, Inc. |
|
11. Appendix |
A comprehensive market research approach was employed to gather and analyze data on the Phishing Simulator Market. In the process, the analysis was also done to analyze the parent market and relevant adjacencies to measure the impact of them on the Phishing Simulator Market. The research methodology encompassed both secondary and primary research techniques, ensuring the accuracy and credibility of the findings.
.jpg)
Secondary Research
Secondary research involved a thorough review of pertinent industry reports, journals, articles, and publications. Additionally, annual reports, press releases, and investor presentations of industry players were scrutinized to gain insights into their market positioning and strategies.
Primary Research
Primary research involved conducting in-depth interviews with industry experts, stakeholders, and market participants across the E-Waste Management ecosystem. The primary research objectives included:
- Validating findings and assumptions derived from secondary research
- Gathering qualitative and quantitative data on market trends, drivers, and challenges
- Understanding the demand-side dynamics, encompassing end-users, component manufacturers, facility providers, and service providers
- Assessing the supply-side landscape, including technological advancements and recent developments
Market Size Assessment
A combination of top-down and bottom-up approaches was utilized to analyze the overall size of the Phishing Simulator Market. These methods were also employed to assess the size of various subsegments within the market. The market size assessment methodology encompassed the following steps:
- Identification of key industry players and relevant revenues through extensive secondary research
- Determination of the industry's supply chain and market size, in terms of value, through primary and secondary research processes
- Calculation of percentage shares, splits, and breakdowns using secondary sources and verification through primary sources
.jpg)
Data Triangulation
To ensure the accuracy and reliability of the market size, data triangulation was implemented. This involved cross-referencing data from various sources, including demand and supply side factors, market trends, and expert opinions. Additionally, top-down and bottom-up approaches were employed to validate the market size assessment.
NA
