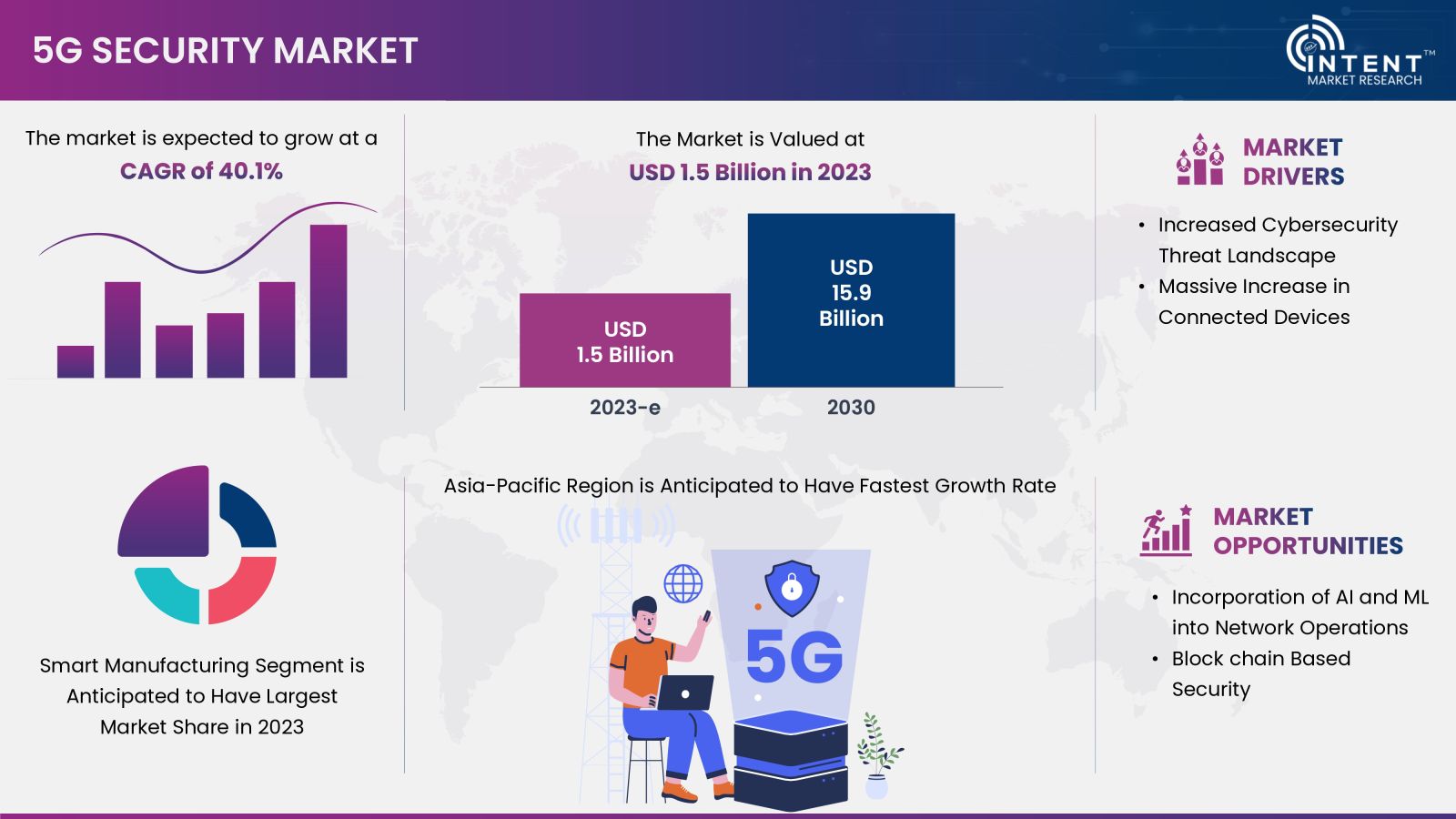
According to Intent Market Research, the 5G Security Market is expected to grow from USD 1.5 billion in 2023-e at a CAGR of 40.1% to touch USD 15.9 billion by 2030. The 5G security market is a competitive market, the prominent players in the global market include AT&T, Atos, Check Point, Ericsson, Fortinet, Huawei, Juniper Network, Nokia, Palo Alto, Singtel, Thales, among others.
5G security is the combined physical and cyber protection for the underlying 5G network infrastructure including hardware and software, the traffic traversing it, and users of the network. 5G security is an area of wireless network security focused on 5G wireless networks. 5G security technologies help protect 5G infrastructure and 5G-enabled devices against data loss, cyber-attacks, hackers, malware, and other threats. Compared to previous generations, 5G makes greater use of virtualization, network slicing, and software-defined networking (SDN), making it vulnerable to new kinds of attacks.
The proliferation of cyber threats, including sophisticated attacks such as ransomware and advanced persistent threats, has created a heightened awareness of the need for robust security measures in 5G networks. This, in turn, drives the 5G security market. However, the complexity of network architecture is restraining the market growth.
Incorporation of AI & ML into network operations offers significant opportunities for the market stakeholders. AI and ML can analyze network patterns to detect and prevent security threats in real time. This proactive approach helps in identifying and mitigating potential vulnerabilities before they can be exploited.
Increased Cybersecurity Threat is Driving the 5G Security Market
The increased cybersecurity threat is a significant driver for the 5G security market. The deployment of 5G networks results in a massive increase in connected devices, including IoT devices and critical infrastructure components. This expanded attack surface provides more entry points for cyber threats, making comprehensive security measures essential. The proliferation of Internet of Things (IoT) devices in 5G networks introduces new security challenges. Many IoT devices may have limited security features, making them susceptible to exploitation by malicious actors.
Addressing these challenges requires a holistic and collaborative approach from industry stakeholders, including telecom operators, technology vendors, regulatory bodies, and cybersecurity experts. The 5G security market plays a vital role in developing and implementing solutions that mitigate these threats and ensure the secure deployment and operation of 5G networks.
5G Security Market Segment Insights
Rapid Adoption of Security Solutions is Driving the Segmental Growth
The rapid adoption of security solutions is a driving force for the 5G security market. The dynamic and sophisticated nature of cyber threats is leading to a heightened awareness of the need for robust security solutions in 5G networks. The increasing frequency and complexity of cyber-attacks drive the adoption of advanced security measures.
As 5G becomes integral to supporting critical infrastructure services such as energy, healthcare, and transportation, the adoption of security solutions becomes imperative. The rapid adoption of security solutions in the 5G space reflects the industry's commitment to building secure, resilient, and trustworthy networks. As 5G technology continues to advance, the ongoing adoption of security solutions remains crucial for safeguarding critical services, ensuring privacy, and maintaining the integrity of the evolving network infrastructure.
Source: Intent Market Research Analysis
Standalone (SA) Architecture of 5G Security to Record Rapid Growth
SA 5G enables end-to-end 5G capabilities without dependencies on legacy networks. This allows for the full realization of 5G's potential in terms of increased data speeds, lower latency, and support for massive IoT deployments. SA 5G architecture supports advanced network slicing capabilities, allowing operators to create isolated and customized virtual networks tailored to specific use cases. This flexibility is essential for accommodating diverse applications with varying requirements.
5G Standalone architecture breaks new ground by using a single radio access technology (RAT). With no 4G legacy setup, or anchoring bands to look after, 5G Standalone enables around 6x faster access to 5G spectrum and massively simplifies planning and execution. Considering the benefits, standalone architecture is expected to grow rapidly in the coming years.
RAN Captured a Major Share of Network Security Segment
RAN security involves implementing robust access control mechanisms and authentication protocols to verify the identity of devices attempting to connect to the network. Unauthorized access to the RAN can lead to security breaches. RAN security measures address potential threats such as interference and jamming that can disrupt wireless communication. Ensuring the reliability of the RAN is vital for maintaining connectivity in the face of such threats.
As 5G networks continue to evolve, the security of the RAN remains a top priority for telecom operators and organizations deploying 5G services. The focus on RAN security reflects its critical role in providing secure and reliable wireless connectivity for a wide range of applications and services. As a result, the segment is estimated to have a larger share in the network security segment.
Higher Adoption due to Security Concerns Increasing the Share of Telecom Operators
Telecom operators are among the primary stakeholders driving the demand for 5G security solutions. The deployment of 5G networks introduces new challenges and requirements for ensuring the security, integrity, and resilience of the infrastructure. Telecom operators, responsible for operating and managing these networks, have specific demands and needs related to 5G security.
The demand for 5G security solutions from telecom operators is driven by the imperative to provide secure and reliable services in an environment with increasing cyber threats and evolving network complexities. As 5G networks continue to advance, the collaboration between telecom operators and security solution providers becomes crucial in building and maintaining secure network infrastructures.
Smart Manufacturing Segment to Hold Major Market Share in 5G Security Market
The adoption of 5G security in smart manufacturing is crucial as industries increasingly leverage 5G technology to transform their manufacturing processes and operations. Smart manufacturing relies heavily on the deployment of Internet of Things (IoT) devices, such as sensors, actuators, and connected machinery. 5G security solutions ensure secure connectivity for these devices, protecting against unauthorized access and data breaches.
The adoption of 5G security in smart manufacturing aligns with the industry's goals of achieving increased efficiency, flexibility, and connectivity. Security measures are integrated into the fabric of 5G-enabled smart manufacturing systems to create a resilient and secure foundation for the next generation of industrial processes.
Manufacturing Industry Sees Growing Adoption of 5G Security Solutions
The deployment of 5G facilitates a higher density of connected devices and sensors in manufacturing environments. This increased connectivity requires robust security solutions to safeguard against potential threats and vulnerabilities. 5G enables the deployment of edge computing in manufacturing, allowing real-time data processing at the edge of the network. Security solutions are essential to protect edge devices and ensure the integrity of data processed locally.
Manufacturing relies on critical infrastructure, including programmable logic controllers (PLCs) and industrial control systems (ICS). Security solutions are essential to protect these critical components from cyber threats and potential disruptions. By utilizing 5G networks, manufacturers can optimize their operations, reduce costs, and stay competitive in a rapidly changing business landscape. Due to benefits associated with this technology, the manufacturing industry is estimated to capture a major market share in 2023.
Asia-Pacific to Grow Exponentially in the Coming Years
The deployment of 5G networks across various countries in the Asia-Pacific has led to an increased focus on securing these networks against potential cyber threats. Countries such as China, South Korea, Japan have been actively deploying and expanding their 5G networks. The rapid deployment of 5G infrastructure creates a demand for security solutions to protect these networks. Additionally, several cities in the Asia-Pacific are undergoing smart city transformations, leveraging 5G technology. The integration of 5G in smart city initiatives necessitates security measures to protect critical services and infrastructure which will lead to rapid market growth during the forecast period.
Major Industry Players are Enhancing their Market Positions By Adopting Several Growth Strategies
Major players operating in the global 5G security market are AT&T, Atos, Check Point, Ericsson, Fortinet, Huawei, Juniper Network, Nokia, Palo Alto, and Thales, among others. Major players have started adopting strategies such as new product launches, merger & acquisitions, and partnership & collaboration to tap the potential market share. Some of the significant developments are mentioned below:
- In February 2023, Atos announced the launch of its new ‘5Guard’ security offering for organizations looking to deploy private 5G networks and for telecom operators looking to enable integrated, automated, and orchestrated security to protect and defend their assets and customers.
- In February 2023, Check Point introduced Infinity Spark, a threat prevention solution that delivers industry leading AI security and integrated connectivity to small and medium-sized businesses (SMBs).
5G Security Market by Coverage
The report provides key insights into the 5G security market, and it focuses on technological developments, trends, and initiatives taken by the government and private players. It delves into market drivers, restraints, opportunities, and challenges that are impacting market growth. It analyses key players as well as the competitive landscape within the global 5G security market.
Report Scope:
|
Report Features |
Description |
|
Market Size (2023-e) |
USD 1.5 Billion |
|
Forecast Revenue (2030) |
USD 15.9 Billion |
|
CAGR (2024-2030) |
40.1% |
|
Base Year for Estimation |
2023-e |
|
Historic Year |
2022 |
|
Forecast Period |
2024-2030 |
|
Report Coverage |
Market Forecast, Market Dynamics, Competitive Landscape, Recent Developments |
|
Segments Covered |
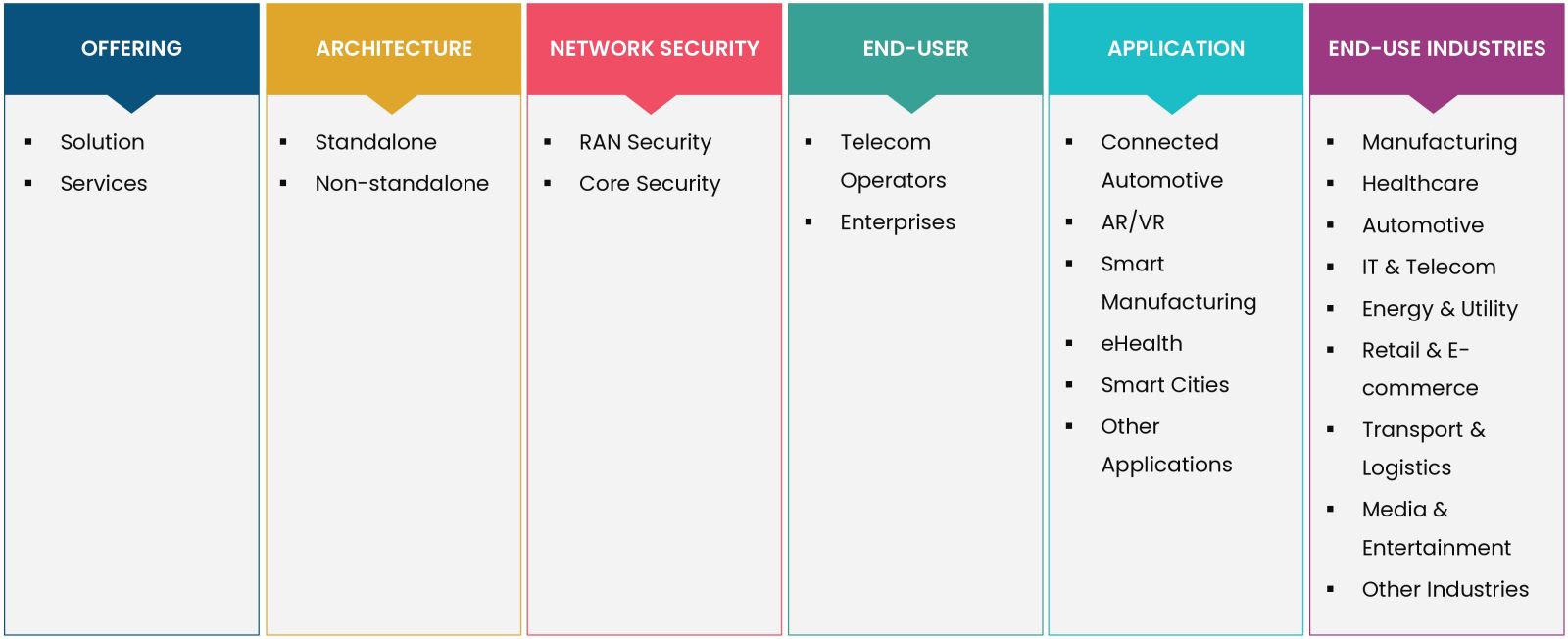
By Offering (Solution, Services); By Architecture (Standalone, Non-standalone); Network Security (RAN Security, Core Security); By End-user (Telecom Operators, Enterprises); By Application (Connected Automotive, AR/VR, Smart Manufacturing, eHealth, Smart Cities, Others); By End-use Industries (Manufacturing, Healthcare, Automotive, IT & Telecom, Energy & Utility, Retail & E-commerce, Transport & Logistics, Media & Entertainment, Other Industries) |
|
Regional Analysis |
North America (US, Canada), Asia-Pacific (China, Japan, South Korea, India), Europe (Germany, France, UK, Italy), Latin America and Middle East & Africa |
|
Competitive Landscape |
AT&T, Atos, Check Point, Ericsson, Fortinet, Huawei, Juniper Network, Nokia, Palo Alto, and Thales, among others. |
|
Customization Scope |
Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. |
|
Purchase Options |
We have three licenses to opt for Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) |
|
1.Introduction |
|
1.1.Market Definition |
|
1.2.Scope of the Study |
|
1.3.Key Stakeholders of the Market |
|
2.Research Methodology |
|
2.1.Research Approach |
|
2.2.Data Collection |
|
2.3.Market Assessment |
|
2.4.Assumptions & Limitations for the Study |
|
3.Executive Summary |
|
4.Market Dynamics |
|
4.1.Drivers |
|
4.1.1.Increased Cybersecurity Threat Landscape |
|
4.1.2.Massive Increase in Connected Devices |
|
4.2.Restraints |
|
4.2.1.High Implementation Costs |
|
4.2.2.Complexity of Network Architecture |
|
4.3.Opportunities |
|
4.3.1. Incorporation of AI and ML into Network Operations |
|
4.4.Challenges |
|
4.4.1.Network Slicing Vulnerabilities |
|
4.4.2.Edge Device Vulnerabilities |
|
5.Market Outlook |
|
5.1.Key 3GPP Security Features of the 5GC |
|
5.2.Overview of the 3GPP 5G Security Standard |
|
5.3.Pricing Analysis |
|
5.4.PESTLE Analysis |
|
5.5.PORTER's Five Forces Analysis |
|
6.Market Size by Offering (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
6.1.Solutions |
|
6.2.Services |
|
7.Market Size by Architecture (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
7.1.Standalone |
|
7.2.Non-standalone |
|
8.Market Size by Network Security (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
8.1.RAN Security |
|
8.2.Core Security |
|
9.Market Size by End-user (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
9.1.Telecom Operator |
|
9.2.Enterprises |
|
10.Market Size by Application (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
10.1. Connected Automotive |
|
10.2. AR/VR |
|
10.3. Smart Manufacturing |
|
10.4. eHealth |
|
10.5. Smart Cities |
|
10.6. Other Applications |
|
11.Market Size by End-use Industries (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
11.1. Manufacturing |
|
11.2. Healthcare |
|
11.3. Automotive |
|
11.4. IT & Telecom |
|
11.5. Energy & Utility |
|
11.6. Retail & E-commerce |
|
11.7. Transport & Logistics |
|
11.8. Media & Entertainment |
|
11.9. Other Industries |
|
12.Regional Outlook, (Market Size & Forecast: USD Billion, 2023 – 2030) |
|
12.1. North America |
|
12.1.1. US |
|
12.1.1.1. US Market Outlook by Type |
|
12.1.1.2. US Market Outlook by Component |
|
12.1.1.3. US Market Outlook by Organization Size |
|
12.1.1.4. US Market Outlook by Application |
|
12.1.1.5. US Market Outlook by End-use Industries |
|
Note: Similar Cross-segmentation for each country will be covered as shown above |
|
12.1.2. Canada |
|
12.2. Asia-Pacific |
|
12.2.1. China |
|
12.2.2. Japan |
|
12.2.3. South Korea |
|
12.2.4. India |
|
12.3. Europe |
|
12.3.1. UK |
|
12.3.2. Germany |
|
12.3.3. France |
|
12.3.4. Italy |
|
12.4. Latin America |
|
12.5. Middle East & Africa |
|
13.Competitive Landscape |
|
13.1. Market Share Analysis |
|
13.2. Key Market Growth Strategies |
|
13.3. Company Strategy Analysis |
|
13.4. Competitive Benchmarking |
|
14.Company Profile |
|
14.1. AT&T |
|
14.2. Atos |
|
14.3. Check Point |
|
14.4. Ericsson |
|
14.5. Fortinet |
|
14.6. Huawei |
|
14.7. Juniper Network |
|
14.8. Nokia |
|
14.9. Palo Alto |
|
14.10. Singtel |
|
14.11. Thales |
|
15.Appendix |
Intent Market Research employs a rigorous methodology to minimize residual errors by carefully defining the scope, validating findings through primary research, and consistently updating our in-house database. This dynamic approach allows us to capture ongoing market fluctuations and adapt to evolving market uncertainties.
The research factors used in our methodology vary depending on the specific market being analysed. To begin with, we incorporate both demand and supply side information into our model to identify and address market gaps. Additionally, we also employ approaches such as Macro-indicator Analysis, Factor Analysis, Value Chain-based Sizing, and forecasting to further increase the accuracy of the numbers and validate the findings.
Research Approach
- Secondary Research Approach: During the initial phase of the research process, we acquire and accumulate extensive data continuously. This data is carefully filtered and validated through a variety of secondary sources.
- Primary Research Approach: Following the consolidation of data gathered through secondary research, we initiate a validation process to verify all the market numbers, assumptions and validate the findings by engaging with subject matter experts.
Data Collection, Analysis and Interpretation:
.jpg)
Research Methodology
Our market research methodology utilizes both top-down and bottom-up approaches to segment and estimate quantitative aspects of the market. We also employ multi-perspective analysis, examining the market from distinct viewpoints.