sales@intentmarketresearch.com
+1 463-583-2713
Zero Trust Architecture Market Size Analysis By Authentication Type (Single-factor Authentication, Multi-factor Authentication), By Solution (Network Security, Endpoint Security, Identity & Access Management (IAM), Data Security, Security Analytics, Threat Intelligence), By Deployment Model (On-Premises, Cloud-based), By End-Use Industry (IT & Telecom, BFSI, Healthcare, Retail), By Organization Size (Small & Medium-sized Enterprises (SMEs), Large Enterprises) & By Region; Global Insights & Forecast (2024 - 2030)
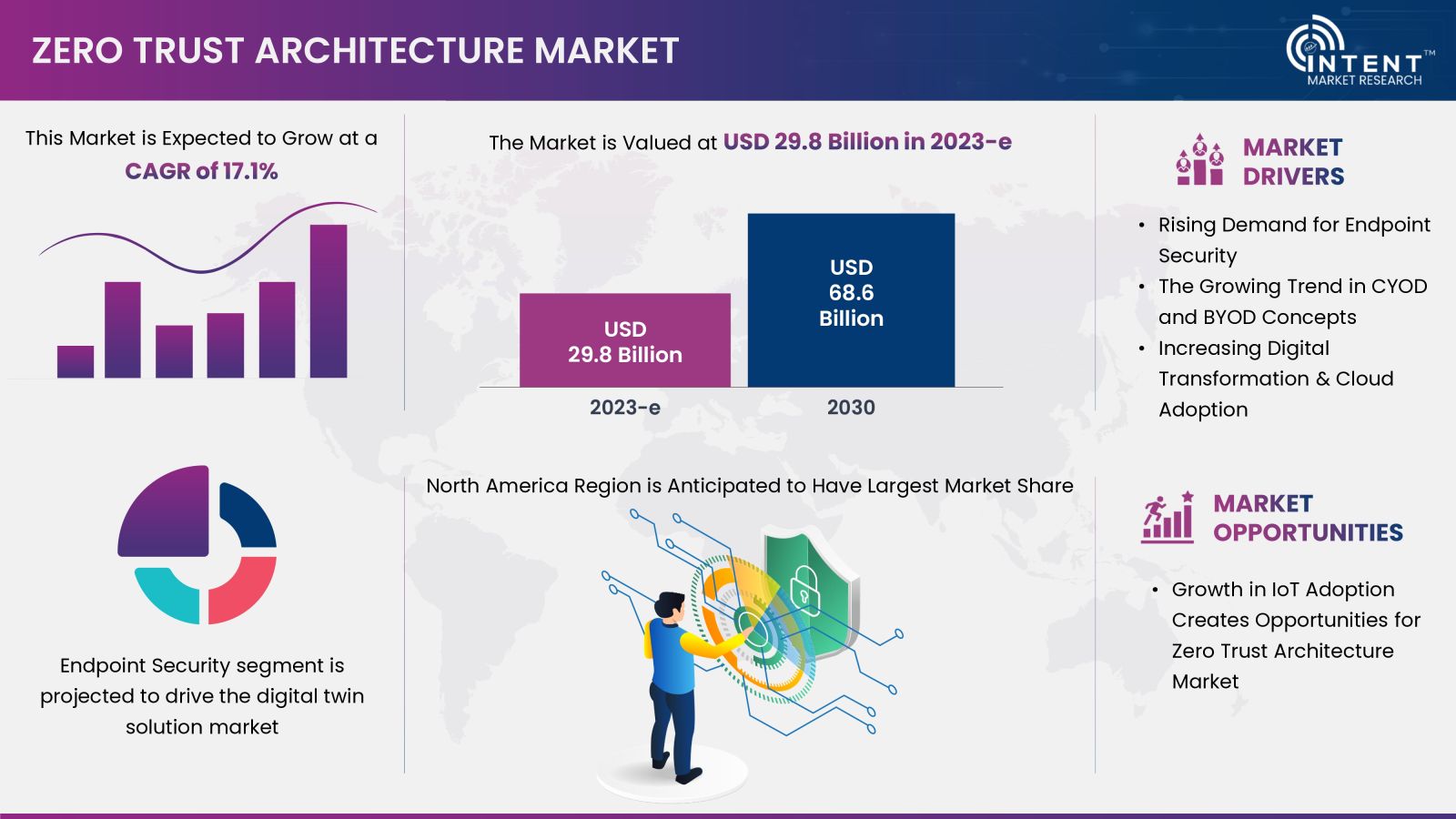
As per Intent Market Research, the Zero Trust Architecture Market was valued at USD 29.8 billion in 2023-e and will surpass USD 68.6 billion by 2030; growing at a CAGR of 17.1% during 2024 - 2030. ZTA has gained prominence as a cybersecurity paradigm, emphasizing the need for continuous verification and strict access controls to enhance overall security.
Zero Trust Architecture (ZTA) is a cybersecurity framework that challenges the traditional notion of trust within a network. In a zero-trust architecture, organizations do not automatically trust any user or system, whether they are inside or outside the corporate network. The zero-trust architecture framework aims to provide a more robust and dynamic approach to cybersecurity, especially in a landscape where traditional perimeter-based security measures may not be sufficient to protect against advanced and persistent threats.
Zero Trust Architecture Market Dynamics
The Growing Trend in CYOD and BYOD Concepts Is Driving the Market Growth
The Bring Your Own Device (BYOD) and Choose Your Own Device (CYOD) trends are becoming significantly more popular across all businesses. ZTA mitigates this risk by implementing a security framework that does not trust devices or users by default. In a zero-trust architecture model, ZTA prioritizes identity-centric security, where user identity plays a crucial role in defining access privileges. It incorporates contextual factors such as device health, location, and user behavior to guide access decisions.
Stringent Authentication Measures have a Huge Impact on User Experience
Strict authentication and authorization measures in zero trust architecture are impacting the user experience. If it’s not implemented properly, it causes frustration, productivity issues, and user resistance. To find the right balance, companies prioritize user-friendly solutions that simplify the authentication process, provide clear access controls, and have intuitive interfaces.
Zero Trust Architecture Market Segment Insights
Rising Demand for Endpoint Security in Various Verticals is Thriving the Market Growth
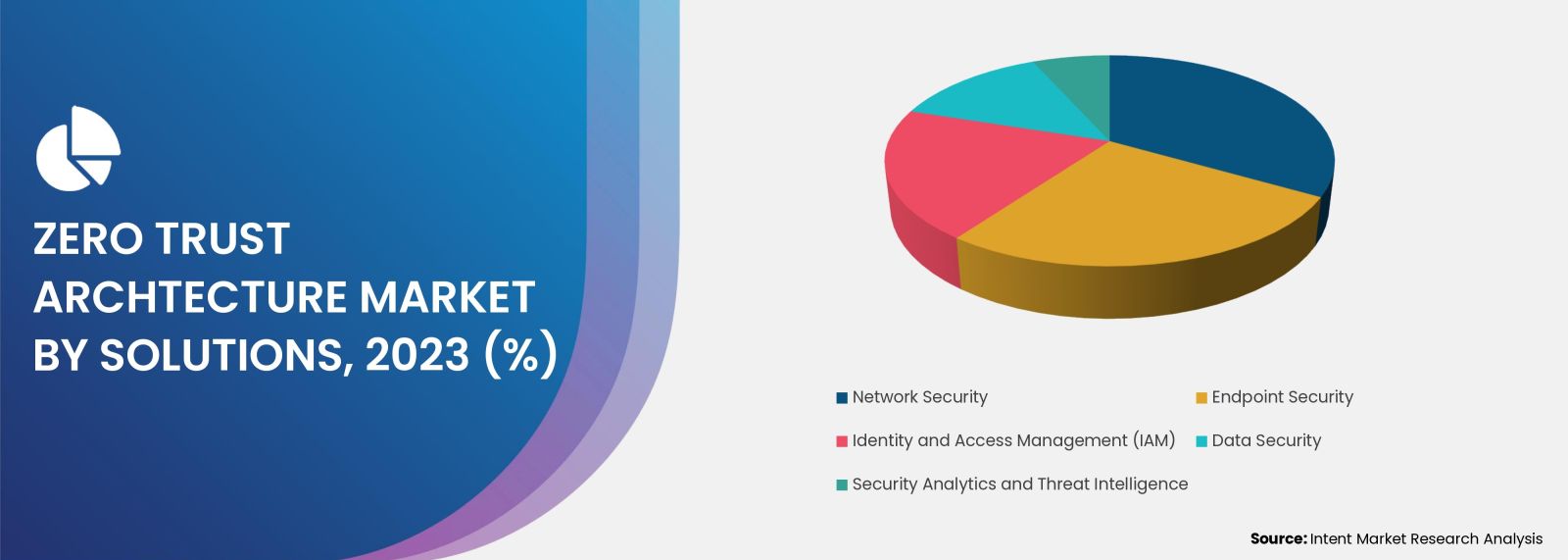
The endpoint security segment is expected to account for the largest share by security type. Growth in the endpoint segment is due to benefits such as improved patch management, insider threat prevention, web content filtering, AI threat mitigation, and cybersecurity optimization. Additionally, companies on the market have developed improved solutions to achieve better traction. The companies are engaged in various strategic initiatives, including alliances, acquisitions, and mergers. In January 2023, cybersecurity provider Xcitium entered into a partnership with communications solutions provider Carrier SI.
Cloud-Based Deployment of Zero Trust Architecture is Strengthening the Market Growth
The cloud-based deployment is expected to show the significant growth rate over the forecast period. The growth of the cloud-based segment is attributed to the comfort and convenience that cloud-based delivery provides. This includes reduced internal resource needs, lower initial costs, continuous monitoring, flexible options, automated backups, and especially effective patch management. The flexibility and scalability of cloud-based deployments is one of the key factors contributing to the growth of the cloud-based market from 2024 to 2030.
Large Enterprises occupy A Dominant Position in ZTA Market
The large enterprise segment accounted for the largest share and expected to witness significant growth from 2024 to 2030, as large enterprises' complex networks, programs, and endpoints require robust solutions to protect data, continuous verification, and recording of authentication in real-time. Enterprises rely solely on maintaining compliance and trusting authorized users with a high risk of internal compromise. The zero trust architecture model treats all authorized users within an enterprise as Zero Trust, granting them the least privileged access.
Increasing Adoption of Multi-Factor Authentication for Real-Time Access Validation & Monitoring Is Encouraging the Market Growth
The multi-factor authentication segment is expected to grow at the highest annual growth rate from 2024 to 2030. Multi-factor authentication, widely adopted across industries for its high security, is a crucial element of the trust zero-trust model. Ensuring robust security, this approach goes beyond the convenience of a single credential element. Multiple layers of real-time access validation and monitoring are imperative to uphold a zero-trust security model, preventing hackers from exploiting a single identification point.
Increasing Adoption of Zero Trust Architecture in IT & Telecom Sector is Propelling Market Growth
IT & telecom sector accounted for the high revenue share in 2023 and is expected to maintain its leading position throughout the forecast period. Cloud-based infrastructure and digital applications are increasingly preferred to collect information and facilitate business, increasing the need for integrated and secure access and networking solutions. As awareness of the benefits and applications of zero-trust architecture increases, it is expected that the adoption of this model will increase significantly.
Regional Insights
The Presence of Key Players is Stimulating the North American Market Growth
The United States, with its inclination toward advanced technology and network automation, is a significant contributor to the growth of the zero-trust architecture market. This is further fueled by the surge in cloud-based services. The market is driven by increasing digitization in end-user industries, with key players such as Cisco, IBM, VMware, Palo Alto Networks, and Akamai Technologies playing a pivotal role. North America's zero trust market is expected to witness substantial growth, driven by increasing cloud migration and the presence of key vendors. Continuous launches of new solutions and growing partnerships among market players will further propel market growth.
Competitive Landscape
Key Players Are Expanding Their Solution Portfolio to Sustain in the Competitive Environment
The market is intensely competitive, with a few major global players holding significant market share. Key players focus on partnerships and collaborations. For instance, Microsoft Entra introduced two innovative products in the Security Service Edge (SSE) arena in July 2023, while Cisco Systems expanded its security portfolio with the Cisco Secure Access solution in June 2023. This solution streamlines access in hybrid work environments. Prominent players include Akamai Technologies, Appgate, Broadcom, Check Point Software Technologies, Cisco, Cloudflare, CrowdStrike, Forcepoint, Fortinet, IBM, Musarubra, Microsoft, Okta, Palo Alto Networks, and Zscaler.
Zero Trust Architecture Market Coverage
The report provides key insights into the zero-trust architecture market, and it focuses on technological developments, trends, and initiatives taken by the government in this sector. The analysis focuses on market drivers, restraints, and opportunities, and examines key players and the competitive landscape within the zero-trust architecture market.
Report Scope
|
Report Features |
Description |
|
Market Size (2023-e) |
USD 29.8 Billion |
|
Forecast Revenue (2030) |
USD 68.6 Billion |
|
CAGR (2024-2030) |
17.1% |
|
Base Year for Estimation |
2023-e |
|
Historic Year |
2022 |
|
Forecast Period |
2024-2030 |
|
Report Coverage |
Revenue Forecast, Market Dynamics, Competitive Landscape, Recent Developments |
|
Segments Covered |
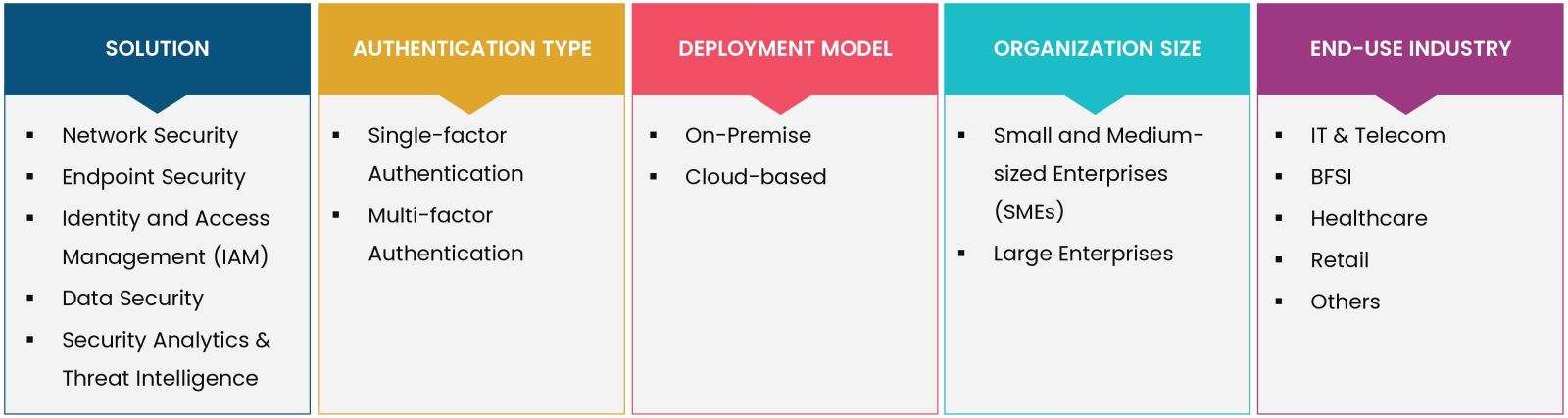
By Authentication Type (Single-factor Authentication and multi-factor Authentication), By Solution (Network Security, Endpoint Security, Identity and Access Management (IAM), Data Security, Security Analytics, and Threat Intelligence), By Deployment Model (On-Premises and cloud-based), By End-Use Industry (IT & Telecom, BFSI, Healthcare, Retail & Others), By Organization Size (Small and Medium-sized Enterprises (SMEs) & Large Enterprises) |
|
Regional Analysis |
North America (US, Canada), Europe (Germany, France, UK, Spain, Italy), Asia-Pacific (China, Japan, South Korea, India), Latin America (Brazil, Mexico, Argentina), Middle East & Africa (Saudi Arabia, South Africa, Turkey, United Arab Emirates) |
|
Competitive Landscape |
Akamai Technologies, Appgate, Broadcom+, Check Point Software, Cisco, Cloudflare, CrowdStrike, Forcepoint, Fortinet, IBM, Musarubra, Microsoft, Okta, Palo Alto Networks, Zscaler |
|
Customization Scope |
Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements |
|
Purchase Options |
We have three licenses to opt for Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) |
|
1. Introduction |
|
1. 1. Study Assumptions and Zero Trust Architecture Market Definition |
|
1.2. Scope of the Study |
|
2. Research Methodology |
|
3. Executive Summary |
|
4. Zero Trust Architecture Market Dynamics |
|
4.1. Market Growth Drivers |
|
4.2 Market Growth Challenges |
|
5. Zero Trust Architecture Market Outlook |
|
5.1. Regulatory Scenario |
|
5.2 Patent Analysis |
|
5.3. PEST Analysis |
|
5.4 PORTER’s Analysis |
|
5.5. Case study |
|
5.6 Technological advances and future opportunity analysis |
|
5.7. Pricing Analysis |
|
5.8 Industry SWOT Analysis |
|
6. Global Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
6.1 Solution |
|
6.1.1 Network Security |
|
6.1.2 Endpoint Security |
|
6.1.3 Identity and Access Management (IAM) |
|
6.1.4 Data Security |
|
6.1.5 Security Analytics and Threat Intelligence |
|
6.2 Authentication Type |
|
6.2.1 Single-factor Authentication |
|
6.2.2 Multi-factor Authentication |
|
6.3 End-Use Industry |
|
6.3.1 IT & Telecom |
|
6.3.2 BFSI |
|
6.3.3 Healthcare |
|
6.3.4 Retail |
|
6.3.5 Others |
|
6.4 Enterprise size |
|
6.4.1 Large Enterprises |
|
6.4.2 Small and Medium Enterprises (SMEs) |
|
6.5 Deployment Mode |
|
6.5.1 Cloud-based |
|
6.5.2 On-premises |
|
6.6 Region |
|
6.6.1 North America |
|
6.6.2 Europe |
|
6.6.3 Asia-Pacific |
|
6.6.4 Latin America |
|
6.6.5 Middle East & Africa |
|
7. North America Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
7.1 Solution |
|
7.1.1 Network Security |
|
7.1.2 Endpoint Security |
|
7.1.3 Identity and Access Management (IAM) |
|
7.1.4 Data Security |
|
7.1.5. Security Analytics and Threat Intelligence |
|
7.2 Authentication Type |
|
7.2.1 Single-factor Authentication |
|
7.2.2 Multi-factor Authentication |
|
7.3 End-Use Industry |
|
7.3.1 IT & Telecom |
|
7.3.2 BFSI |
|
7.3.3 Healthcare |
|
7.3.4 Retail |
|
7.3.5 Others |
|
7.4 Enterprise size |
|
7.4.1 Large Enterprises |
|
7.4.2 Small and Medium Enterprises (SMEs) |
|
7.5 Deployment Mode |
|
7.5.1 Cloud-based |
|
7.5.2 On-premises |
|
7.6 Country |
|
7.6.1 United States |
|
7.6.1.1 Solution |
|
7.6.1.1.1 Network Security |
|
7.6.1.1.2 Endpoint Security |
|
7.6.1.1.3 Identity and Access Management (IAM) |
|
7.6.1.1.4 Data Security |
|
7.6.1.1.5 Security Analytics and Threat Intelligence |
|
7.6.1.2 Authentication Type |
|
7.6.1.2.1 Single-factor Authentication |
|
7.6.1.2.2 Multi-factor Authentication |
|
7.6.1.3 End-Use Industry |
|
7.6.1.3.1 IT & Telecom |
|
7.6.1.3.2 BFSI |
|
7.6.1.3.3 Healthcare |
|
7.6.1.3.4 Retail |
|
7.6.1.3.4 Others |
|
7.6.1.4 Enterprise size |
|
7.6.1.4.1 Large Enterprises |
|
7.6.1.4.2 Small and Medium Enterprises (SMEs) |
|
7.6.1.5 Deployment Mode |
|
7.6.1.5.1 Cloud-based |
|
7.6.1.5.2 On-premises |
|
7.6.2 Canada |
|
7.6.2.1 Solution |
|
7.6.2.1.1 Network Security |
|
7.6.2.1.2 Endpoint Security |
|
7.6.2.1.3 Identity and Access Management (IAM) |
|
7.6.2.1.4 Data Security |
|
7.6.2.1.5 Security Analytics and Threat Intelligence |
|
7.6.2.2 Authentication Type |
|
7.6.2.2.1 Single-factor Authentication |
|
7.6.2.2.2 Multi-factor Authentication |
|
7.6.2.3 End-Use Industry |
|
7.6.2.3.1 IT & Telecom |
|
7.6.2.3.2 BFSI |
|
7.6.2.3.3 Healthcare |
|
7.6.2.3.4 Retail |
|
7.6.2.3.4 Others |
|
7.6.2.4 Enterprise size |
|
7.6.2.4.1 Large Enterprises |
|
7.6.2.4.2 Small and Medium Enterprises (SMEs) |
|
7.6.2.5 Deployment Mode |
|
7.6.2.5.1 Cloud-based |
|
7.6.2.5.2 On-premises |
|
8. Europe Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
8.1 Solution |
|
8.1.1 Network Security |
|
8.1.2 Endpoint Security |
|
8.1.3 Identity and Access Management (IAM) |
|
8.1.4 Data Security |
|
8.1.5 Security Analytics and Threat Intelligence |
|
8.2 Authentication Type |
|
8.2.1 Single-factor Authentication |
|
8.2.2 Multi-factor Authentication |
|
8.3 End-Use Industry |
|
8.3.1 IT & Telecom |
|
8.3.2 BFSI |
|
8.3.3 Healthcare |
|
8.3.4 Retail |
|
8.3.5 Others |
|
8.4 Enterprise size |
|
8.4.1 Large Enterprises |
|
8.4.2 Small and Medium Enterprises (SMEs) |
|
8.5 Deployment Mode |
|
8.5.1 Cloud-based |
|
8.5.2 On-premises |
|
8.6 Country |
|
8.6.1 United Kingdom |
|
8.6.1.1 Solution |
|
8.6.1.1.1 Network Security |
|
8.6.1.1.2 Endpoint Security |
|
8.6.1.1.3 Identity and Access Management (IAM) |
|
8.6.1.1.4 Data Security |
|
8.6.1.1.5 Security Analytics and Threat Intelligence |
|
8.6.1.2 Authentication Type |
|
8.6.1.2.1 Single-factor Authentication |
|
8.6.1.2.2 Multi-factor Authentication |
|
8.6.1.3 End-Use Industry |
|
8.6.1.3.1 IT & Telecom |
|
8.6.1.3.2 BFSI |
|
8.6.1.3.3 Healthcare |
|
8.6.1.3.4 Retail |
|
8.6.1.3.4 Others |
|
8.6.1.4 Enterprise size |
|
8.6.1.4.1 Large Enterprises |
|
8.6.1.4.2 Small and Medium Enterprises (SMEs) |
|
8.6.1.5 Deployment Mode |
|
8.6.1.5.1 Cloud-based |
|
8.6.1.5.2 On-premises |
|
8.6.2 France |
|
8.6.2.1 Solution |
|
8.6.2.1.1 Network Security |
|
8.6.2.1.2 Endpoint Security |
|
8.6.2.1.3 Identity and Access Management (IAM) |
|
8.6.2.1.4 Data Security |
|
8.6.2.1.5 Security Analytics and Threat Intelligence |
|
8.6.2.2 Authentication Type |
|
8.6.2.2.1 Single-factor Authentication |
|
8.6.2.2.2 Multi-factor Authentication |
|
8.6.2.3 End-Use Industry |
|
8.6.2.3.1 IT & Telecom |
|
8.6.2.3.2 BFSI |
|
8.6.2.3.3 Healthcare |
|
8.6.2.3.4 Retail |
|
8.6.2.3.4 Others |
|
8.6.2.4 Enterprise size |
|
8.6.2.4.1 Large Enterprises |
|
8.6.2.4.2 Small and Medium Enterprises (SMEs) |
|
8.6.2.5 Deployment Mode |
|
8.6.2.5.1 Cloud-based |
|
8.6.2.5.2 On-premises |
|
8.6.3 Germany |
|
8.6.3.1 Solution |
|
8.6.3.1.1 Network Security |
|
8.6.3.1.2 Endpoint Security |
|
8.6.3.1.3 Identity and Access Management (IAM) |
|
8.6.3.1.4 Data Security |
|
8.6.3.1.5 Security Analytics and Threat Intelligence |
|
8.6.3.2 Authentication Type |
|
8.6.3.2.1 Single-factor Authentication |
|
8.6.3.2.2 Multi-factor Authentication |
|
8.6.3.3 End-Use Industry |
|
8.6.3.3.1 IT & Telecom |
|
8.6.3.3.2 BFSI |
|
8.6.3.3.3 Healthcare |
|
8.6.3.3.4 Retail |
|
8.6.3.3.4 Others |
|
8.6.3.4 Enterprise size |
|
8.6.3.4.1 Large Enterprises |
|
8.6.3.4.2 Small and Medium Enterprises (SMEs) |
|
8.6.3.5 Deployment Mode |
|
8.6.3.5.1 Cloud-based |
|
8.6.3.5.2 On-premises |
|
8.6.4 Italy |
|
8.6.4.1 Solution |
|
8.6.4.1.1 Network Security |
|
8.6.4.1.2 Endpoint Security |
|
8.6.4.1.3 Identity and Access Management (IAM) |
|
8.6.4.1.4 Data Security |
|
8.6.4.1.5 Security Analytics and Threat Intelligence |
|
8.6.4.2 Authentication Type |
|
8.6.4.2.1 Single-factor Authentication |
|
8.6.4.2.2 Multi-factor Authentication |
|
8.6.4.3 End-Use Industry |
|
8.6.4.3.1 IT & Telecom |
|
8.6.4.3.2 BFSI |
|
8.6.4.3.3 Healthcare |
|
8.6.4.3.4 Retail |
|
8.6.4.3.4 Others |
|
8.6.4.4 Enterprise size |
|
8.6.4.4.1 Large Enterprises |
|
8.6.4.4.2 Small and Medium Enterprises (SMEs) |
|
8.6.4.5 Deployment Mode |
|
8.6.4.5.1 Cloud-based |
|
8.6.4.5.2 On-premises |
|
9. Asia-Pacific Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
9.1 Solution |
|
9.1.1 Network Security |
|
9.1.2 Endpoint Security |
|
9.1.3 Identity and Access Management (IAM) |
|
9.1.4 Data Security |
|
9.1.5 Security Analytics and Threat Intelligence |
|
9.2 Authentication Type |
|
9.2.1 Single-factor Authentication |
|
9.2.2 Multi-factor Authentication |
|
9.3 End-Use Industry |
|
9.3.1 IT & Telecom |
|
9.3.2 BFSI |
|
9.3.3 Healthcare |
|
9.3.4 Retail |
|
9.3.5 Others |
|
9.4 Enterprise size |
|
9.4.1 Large Enterprises |
|
9.4.2 Small and Medium Enterprises (SMEs) |
|
9.5 Deployment Mode |
|
9.5.1 Cloud-based |
|
9.5.2 On-premises |
|
9.6 Country |
|
9.6.1 China |
|
9.6.1.1 Solution |
|
9.6.1.1.1 Network Security |
|
9.6.1.1.2 Endpoint Security |
|
9.6.1.1.3 Identity and Access Management (IAM) |
|
9.6.1.1.4 Data Security |
|
9.6.1.1.5 Security Analytics and Threat Intelligence |
|
9.6.1.2 Authentication Type |
|
9.6.1.2.1 Single-factor Authentication |
|
9.6.1.2.2 Multi-factor Authentication |
|
9.6.1.3 End-Use Industry |
|
9.6.1.3.1 IT & Telecom |
|
9.6.1.3.2 BFSI |
|
9.6.1.3.3 Healthcare |
|
9.6.1.3.4 Retail |
|
9.6.1.3.4 Others |
|
9.6.1.4 Enterprise size |
|
9.6.1.4.1 Large Enterprises |
|
9.6.1.4.2 Small and Medium Enterprises (SMEs) |
|
9.6.1.5 Deployment Mode |
|
9.6.1.5.1 Cloud-based |
|
9.6.1.5.2 On-premises |
|
9.6.2 Japan |
|
9.6.2.1 Solution |
|
9.6.2.1.1 Network Security |
|
9.6.2.1.2 Endpoint Security |
|
9.6.2.1.3 Identity and Access Management (IAM) |
|
9.6.2.1.4 Data Security |
|
9.6.2.1.5 Security Analytics and Threat Intelligence |
|
9.6.2.2 Authentication Type |
|
9.6.2.2.1 Single-factor Authentication |
|
9.6.2.2.2 Multi-factor Authentication |
|
9.6.2.3 End-Use Industry |
|
9.6.2.3.1 IT & Telecom |
|
9.6.2.3.2 BFSI |
|
9.6.2.3.3 Healthcare |
|
9.6.2.3.4 Retail |
|
9.6.2.3.4 Others |
|
9.6.2.4 Enterprise size |
|
9.6.2.4.1 Large Enterprises |
|
9.6.2.4.2 Small and Medium Enterprises (SMEs) |
|
9.6.2.5 Deployment Mode |
|
9.6.2.5.1 Cloud-based |
|
9.6.2.5.2 On-premises |
|
9.6.3 India |
|
9.6.3.1 Solution |
|
9.6.3.1.1 Network Security |
|
9.6.3.1.2 Endpoint Security |
|
9.6.3.1.3 Identity and Access Management (IAM) |
|
9.6.3.1.4 Data Security |
|
9.6.3.1.5 Security Analytics and Threat Intelligence |
|
9.6.3.2 Authentication Type |
|
9.6.3.2.1 Single-factor Authentication |
|
9.6.3.2.2 Multi-factor Authentication |
|
9.6.3.3 End-Use Industry |
|
9.6.3.3.1 IT & Telecom |
|
9.6.3.3.2 BFSI |
|
9.6.3.3.3 Healthcare |
|
9.6.3.3.4 Retail |
|
9.6.3.3.4 Others |
|
9.6.3.4 Enterprise size |
|
9.6.3.4.1 Large Enterprises |
|
9.6.3.4.2 Small and Medium Enterprises (SMEs) |
|
9.6.3.5 Deployment Mode |
|
9.6.3.5.1 Cloud-based |
|
9.6.3.5.2 On-premises |
|
9.6.4 South Korea |
|
9.6.4.1 Solution |
|
9.6.4.1.1 Network Security |
|
9.6.4.1.2 Endpoint Security |
|
9.6.4.1.3 Identity and Access Management (IAM) |
|
9.6.4.1.4 Data Security |
|
9.6.4.1.5 Security Analytics and Threat Intelligence |
|
9.6.4.2 Authentication Type |
|
9.6.4.2.1 Single-factor Authentication |
|
9.6.4.2.2 Multi-factor Authentication |
|
9.6.4.3 End-Use Industry |
|
9.6.4.3.1 IT & Telecom |
|
9.6.4.3.2 BFSI |
|
9.6.4.3.3 Healthcare |
|
9.6.4.3.4 Retail |
|
9.6.4.3.4 Others |
|
9.6.4.4 Enterprise size |
|
9.6.4.4.1 Large Enterprises |
|
9.6.4.4.2 Small and Medium Enterprises (SMEs) |
|
9.6.4.5 Deployment Mode |
|
9.6.4.5.1 Cloud-based |
|
9.6.4.5.2 On-premises |
|
10. Latin America Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
10.1 Solution |
|
10.1.1 Network Security |
|
10.1.2 Endpoint Security |
|
10.1.3 Identity and Access Management (IAM) |
|
10.1.4 Data Security |
|
10.1.5 Security Analytics and Threat Intelligence |
|
10.2 Authentication Type |
|
10.2.1 Single-factor Authentication |
|
10.2.2 Multi-factor Authentication |
|
10.3 End-Use Industry |
|
10.3.1 IT & Telecom |
|
10.3.2 BFSI |
|
10.3.3 Healthcare |
|
10.3.4 Retail |
|
10.3.5 Others |
|
10.4 Enterprise size |
|
10.4.1 Large Enterprises |
|
10.4.2 Small and Medium Enterprises (SMEs) |
|
10.5 Deployment Mode |
|
10.5.1 Cloud-based |
|
10.5.2 On-premises |
|
10.6 Country |
|
10.6.1 Brazil |
|
10.6.1.1 Solution |
|
10.6.1.1.1 Network Security |
|
10.6.1.1.2 Endpoint Security |
|
10.6.1.1.3 Identity and Access Management (IAM) |
|
10.6.1.1.4 Data Security |
|
10.6.1.1.5 Security Analytics and Threat Intelligence |
|
10.6.1.2 Authentication Type |
|
10.6.1.2.1 Single-factor Authentication |
|
10.6.1.2.2 Multi-factor Authentication |
|
10.6.1.3 End-Use Industry |
|
10.6.1.3.1 IT & Telecom |
|
10.6.1.3.2 BFSI |
|
10.6.1.3.3 Healthcare |
|
10.6.1.3.4 Retail |
|
10.6.1.3.4 Others |
|
10.6.1.4 Enterprise size |
|
10.6.1.4.1 Large Enterprises |
|
10.6.1.4.2 Small and Medium Enterprises (SMEs) |
|
10.6.1.5 Deployment Mode |
|
10.6.1.5.1 Cloud-based |
|
10.6.1.5.2 On-premises |
|
10.6.2 Mexico |
|
10.6.2.1 Solution |
|
10.6.2.1.1 Network Security |
|
10.6.2.1.2 Endpoint Security |
|
10.6.2.1.3 Identity and Access Management (IAM) |
|
10.6.2.1.4 Data Security |
|
10.6.2.1.5 Security Analytics and Threat Intelligence |
|
10.6.2.2 Authentication Type |
|
10.6.2.2.1 Single-factor Authentication |
|
10.6.2.2.2 Multi-factor Authentication |
|
10.6.2.3 End-Use Industry |
|
10.6.2.3.1 IT & Telecom |
|
10.6.2.3.2 BFSI |
|
10.6.2.3.3 Healthcare |
|
10.6.2.3.4 Retail |
|
10.6.2.3.4 Others |
|
10.6.2.4 Enterprise size |
|
10.6.2.4.1 Large Enterprises |
|
10.6.2.4.2 Small and Medium Enterprises (SMEs) |
|
10.6.2.5 Deployment Mode |
|
10.6.2.5.1 Cloud-based |
|
10.6.2.5.2 On-premises |
|
10.6.3 Argentina |
|
10.6.3.1 Solution |
|
10.6.3.1.1 Network Security |
|
10.6.3.1.2 Endpoint Security |
|
10.6.3.1.3 Identity and Access Management (IAM) |
|
10.6.3.1.4 Data Security |
|
10.6.3.1.5 Security Analytics and Threat Intelligence |
|
10.6.3.2 Authentication Type |
|
10.6.3.2.1 Single-factor Authentication |
|
10.6.3.2.2 Multi-factor Authentication |
|
10.6.3.3 End-Use Industry |
|
10.6.3.3.1 IT & Telecom |
|
10.6.3.3.2 BFSI |
|
10.6.3.3.3 Healthcare |
|
10.6.3.3.4 Retail |
|
10.6.3.3.4 Others |
|
10.6.3.4 Enterprise size |
|
10.6.3.4.1 Large Enterprises |
|
10.6.3.4.2 Small and Medium Enterprises (SMEs) |
|
10.6.3.5 Deployment Mode |
|
10.6.3.5.1 Cloud-based |
|
10.6.3.5.2 On-premises |
|
11. Middle East & Africa Zero Trust Architecture Market Segmentation (Market Size & Forecast: USD Billion, 2024 – 2030) |
|
11.1 Solution |
|
11.1.1 Network Security |
|
11.1.2 Endpoint Security |
|
11.1.3 Identity and Access Management (IAM) |
|
11.1.4 Data Security |
|
11.1.5 Security Analytics and Threat Intelligence |
|
11.2 Authentication Type |
|
11.2.1 Single-factor Authentication |
|
11.2.2 Multi-factor Authentication |
|
11.3 End-Use Industry |
|
11.3.1 IT & Telecom |
|
11.3.2 BFSI |
|
11.3.3 Healthcare |
|
11.3.4 Retail |
|
11.3.5 Others |
|
11.4 Enterprise size |
|
11.4.1 Large Enterprises |
|
11.4.2 Small and Medium Enterprises (SMEs) |
|
11.5 Deployment Mode |
|
11.5.1 Cloud-based |
|
11.5.2 On-premises |
|
11.6 Country |
|
11.6.1 Saudi Arabia |
|
11.6.1.1 Solution |
|
11.6.1.1.1 Network Security |
|
11.6.1.1.2 Endpoint Security |
|
11.6.1.1.3 Identity and Access Management (IAM) |
|
11.6.1.1.4 Data Security |
|
11.6.1.1.5 Security Analytics and Threat Intelligence |
|
11.6.1.2 Authentication Type |
|
11.6.1.2.1 Single-factor Authentication |
|
11.6.1.2.2 Multi-factor Authentication |
|
11.6.1.3 End-Use Industry |
|
11.6.1.3.1 IT & Telecom |
|
11.6.1.3.2 BFSI |
|
11.6.1.3.3 Healthcare |
|
11.6.1.3.4 Retail |
|
11.6.1.3.4 Others |
|
11.6.1.4 Enterprise size |
|
11.6.1.4.1 Large Enterprises |
|
11.6.1.4.2 Small and Medium Enterprises (SMEs) |
|
11.6.1.5 Deployment Mode |
|
11.6.1.5.1 Cloud-based |
|
11.6.1.5.2 On-premises |
|
11.6.2 South Africa |
|
11.6.2.1 Solution |
|
11.6.2.1.1 Network Security |
|
11.6.2.1.2 Endpoint Security |
|
11.6.2.1.3 Identity and Access Management (IAM) |
|
11.6.2.1.4 Data Security |
|
11.6.2.1.5 Security Analytics and Threat Intelligence |
|
11.6.2.2 Authentication Type |
|
11.6.2.2.1 Single-factor Authentication |
|
11.6.2.2.2 Multi-factor Authentication |
|
11.6.2.3 End-Use Industry |
|
11.6.2.3.1 IT & Telecom |
|
11.6.2.3.2 BFSI |
|
11.6.2.3.3 Healthcare |
|
11.6.2.3.4 Retail |
|
11.6.2.3.4 Others |
|
11.6.2.4 Enterprise size |
|
11.6.2.4.1 Large Enterprises |
|
11.6.2.4.2 Small and Medium Enterprises (SMEs) |
|
11.6.2.5 Deployment Mode |
|
11.6.2.5.1 Cloud-based |
|
11.6.2.5.2 On-premises |
|
11.6.3 United Arab Emirates |
|
11.6.3.1 Solution |
|
11.6.3.1.1 Network Security |
|
11.6.3.1.2 Endpoint Security |
|
11.6.3.1.3 Identity and Access Management (IAM) |
|
11.6.3.1.4 Data Security |
|
11.6.3.1.5 Security Analytics and Threat Intelligence |
|
11.6.3.2 Authentication Type |
|
11.6.3.2.1 Single-factor Authentication |
|
11.6.3.2.2 Multi-factor Authentication |
|
11.6.3.3 End-Use Industry |
|
11.6.3.3.1 IT & Telecom |
|
11.6.3.3.2 BFSI |
|
11.6.3.3.3 Healthcare |
|
11.6.3.3.4 Retail |
|
11.6.3.3.4 Others |
|
11.6.3.4 Enterprise size |
|
11.6.3.4.1 Large Enterprises |
|
11.6.3.4.2 Small and Medium Enterprises (SMEs) |
|
11.6.3.5 Deployment Mode |
|
11.6.3.5.1 Cloud-based |
|
11.6.3.5.2 On-premises |
|
12. Competitive Landscape |
|
12.1 Company Market Share Analysis |
|
12.2 Competitive Matrix |
|
12.2 Product Benchmarking |
|
12.3 Company Profiles (Manufacturers of Zero Trust Architecture) |
|
12.3.1 Akamai Technologies |
|
12.3.1.1 Company Synopsis |
|
12.3.1.2 Company Financials |
|
12.3.1.3 Product/ Service Portfolio |
|
12.3.1.4 Recent Developments |
|
12.3.2 Appgate |
|
12.3.3 Broadcom+ |
|
12.3.4 Check Point Software Technologies |
|
12.3.5 Cisco Systems |
|
12.3.6 Cloudflare |
|
12.3.7 CrowdStrike |
|
12.3.8 Forcepoint |
|
12.3.9 Fortinet |
|
12.3.10 IBM |
|
12.3.11 Musarubra US LLC |
|
12.3.12 Microsoft |
|
12.3.13 Okta |
|
12.3.14 Palo Alto Networks |
|
12.3.15 Zscaler |
|
12.4 Company Profiles (Demand Side) |
|
12.4.1 Intel Corporation |
|
12.4.1.1 Company Synopsis |
|
12.3.1.2 Company Financials |
|
12.3.1.3 Product/ Service Portfolio |
|
12.3.1.4 Recent Developments |
|
12.4.2 Samsung Electronics |
|
12.4.3 Taiwan Semiconductor Manufacturing Company (TSMC) |
|
12.4.4 NVIDIA Corporation |
|
12.4.5 Advanced Micro Devices (AMD) |
|
13. Analyst Recommendations |
Let us connect with you TOC
Intent Market Research employs a rigorous methodology to minimize residual errors by carefully defining the scope, validating findings through primary research, and consistently updating our in-house database. This dynamic approach allows us to capture ongoing market fluctuations and adapt to evolving market uncertainties.
The research factors used in our methodology vary depending on the specific market being analyzed. To begin with, we incorporate both demand and supply side information into our model to identify and address market gaps. Additionally, we also employ approaches such as Macro-indicator Analysis, Factor Analysis, Value Chain-Based Sizing, and forecasting to further increase the accuracy of the numbers and validate the findings.
Research Approach
- Secondary Research Approach: During the initial phase of the research process, we acquire and accumulate extensive data continuously. This data is carefully filtered and validated through a variety of secondary sources.
- Primary Research Approach: Following the consolidation of data gathered through secondary research, we initiate a validation process to verify all the market numbers, and assumptions and validate the findings by engaging with subject matter experts.
Data Collection, Analysis and Interpretation:
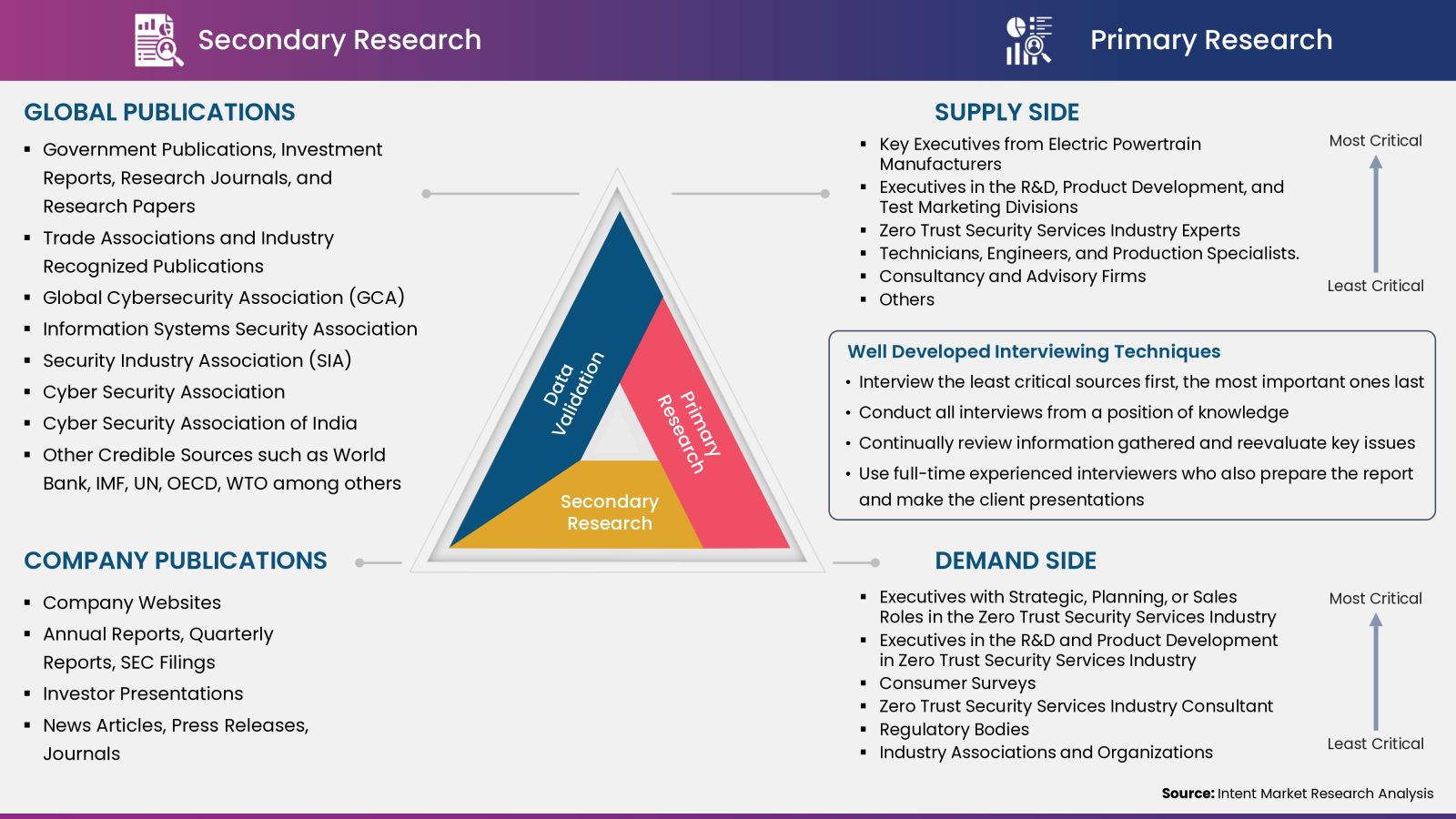
Research Methodology
Our market research methodology utilizes both top-down and bottom-up approaches to segment and estimate quantitative aspects of the market. We also employ multi-perspective analysis, examining the market from distinct viewpoints.
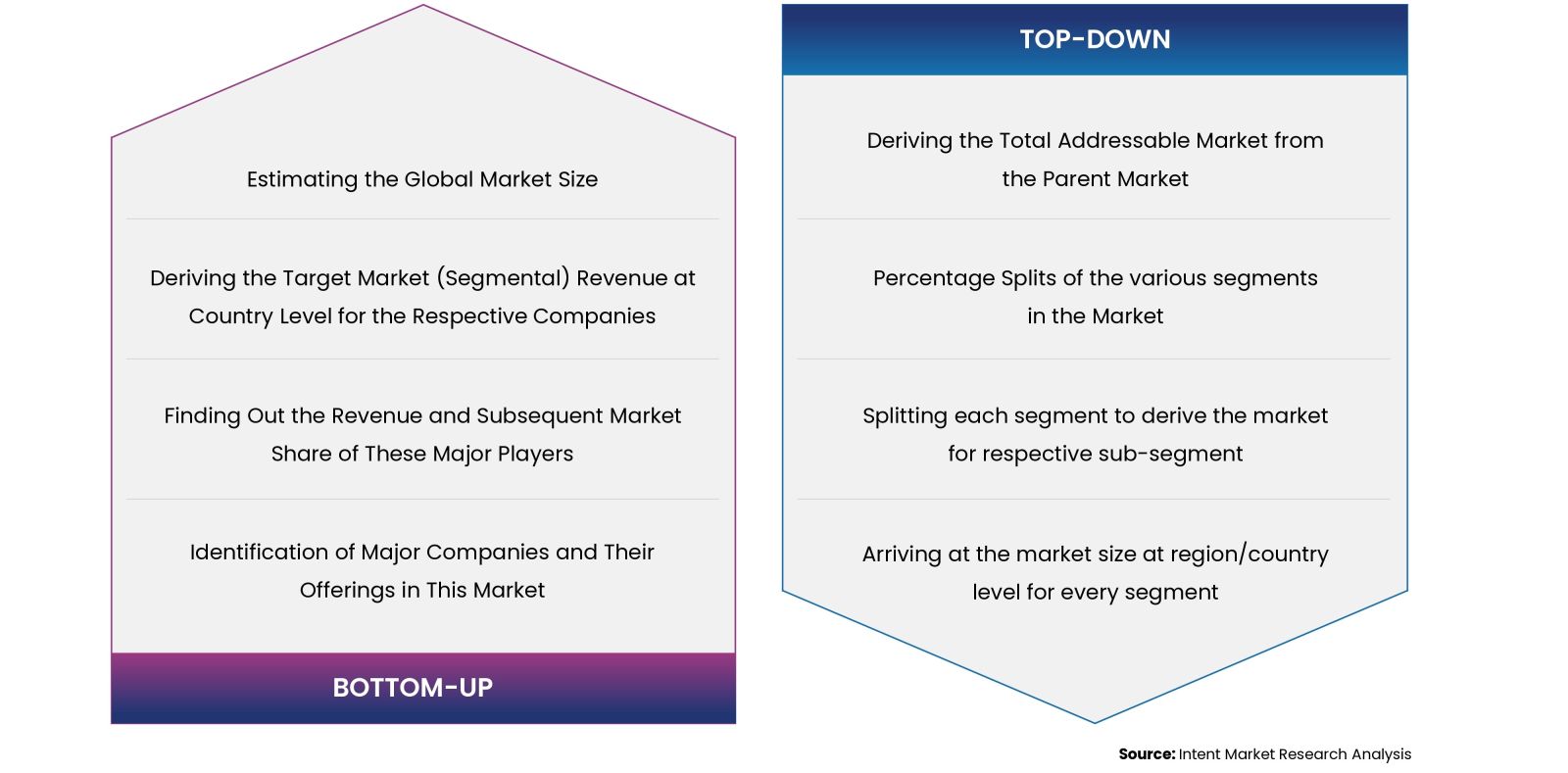

Available Formats


